The basic foundation of security monitoring, detection and response depends on the detection logic/rules that you have. Once these sets of conditions are met, only then an alert is triggered. The alert is then further investigated by a SOC team based on flagged Indicators of Compromise (IOCs) for suspicious or malicious activity before alerting the Incident Handling team within the organization for remediation.
In this blog, we will review how SIEM alerts are typically generated and ideas to help security teams find what matters before it’s too late.
Step 1 - Logs and Attack Coverage
A good strategy to start with is to identify what devices/assets you would like to integrate with your SIEM. Planning is a crucial step — which many organizations fail to do. This results in their SOC teams just project managing a list of devices to onboard and getting submerged in a flood of Service Requests only to question the ROI of the SIEM and SOC team’s efforts later.
“Failing to plan is planning to fail”
Here are three steps that you can use as a checklist to plan and execute data onboarding -
- Identify critical assets (Endpoints, Servers, Applications, Network and Security Devices)
- Create a list of these assets with details - Name, Device Type, IP Address, Vendor, Network Segment and log format your SIEM is compatible with.
- Setup a call with your internal device/application business teams to forward logs to your SIEM.
Once the above steps are completed, ensure you spend a good amount of time (at least 3 to 4 months) to reflect on what use cases are triggered and what optimizations can be done based on trend or type of activities that you see. This is extremely important before deciding to onboard next batch of devices.
It’s important to set aside a good amount of time to:
- Check if logs are parsed properly.
- Understand the kind of use cases triggered.
- Optimize the active/enabled use cases to reduce false positives as much as possible.
- Take note of the attack coverage from MITRE ATT&CK framework point of view.
Here is a blog on how to plan your data ingestion strategy: Understanding Machine Data and it's relevance to security.
Step 2 - Set up a Content Life Cycle Framework
Once you have completed Step 1 - the next phase is to implement and execute the content life cycle as mentioned in the following flow diagram:
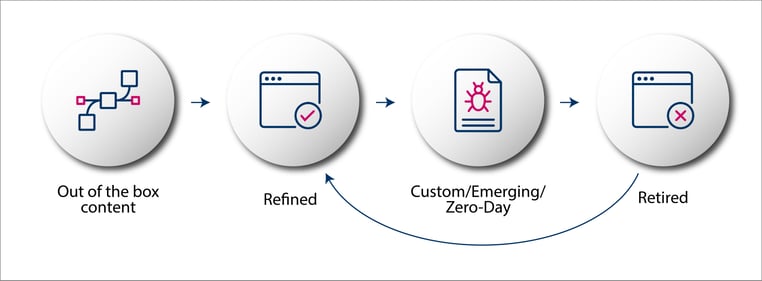 Content Life Cycle Framework
Content Life Cycle Framework
The idea is to segregate your use case content in 4 stages going forward. While data onboarding for remaining devices can be an ongoing process by your integration team, your content/threat hunting team can focus on the following four stages while using the SIEM:
- Pre-Built Content - Identify use cases that get activated by default once you ingest from a new log sources. Keep an eye for use cases that are activated and aligned with the MITRE ATT&CK framework over time. Revisit your integrations or log source configurations to ensure adequate coverage across various Tactics, Techniques and PRocedures (TTPs).
- Refined Content - Refine/Modify the activated use cases/detection logic based on your organization’s environment. Setup appropriate baselines or tweak data filters to minimize false positives or suppress false positive alerts by marking the signals/alerts as such.
- Custom/Emerging/Zero-Day Content - This continuous engagement comprises building custom use cases either as a response to a new detection rule for attacks released in the wild or as per customer requirement within the organization, e.g. list of domains whitelisted in ACLs by DLP team but are flagged as malicious by Threat Intelligence vendors or suggested by Red Teams as an outcome of their assessment.
- Retired Content - It is essential to retire use cases that are not relevant anymore e.g. use cases related to an application that is not used anymore or is decommissioned.
Step 3 - Monitor and Improvise
It is essential to enforce and emphasize the process/framework of the content life cycle discussed above by Organizations. It is imperative for SOC/Security analysts to understand their organization’s unique network architecture so as to customize and derive the best security value unique to their organization without ingesting every IT device that exists. Keep refining and updating the content as per your environment's attack surface.
Takeaways
These are just some techniques/frameworks for security/SOC teams to overcome strategic and planning gaps associated with crafting alerts for data ingested by a SIEM. It’s not always as easy as raising an alert for a use case, instead the analysts must consider the organization’s environmental contexts, concerns and what a suspicious activity might look like.
Vendors that offer managed SIEM services or SIEM products will help you to plan and prioritize IT assets based on their criticality to your business and better leverage automated detection and validation to detect anomalies faster.

