Introduction
A SOC analyst plays a vital role in identifying and investigating potential security incidents. Their primary objective is to validate the threats identified in a SIEM and take appropriate action. Unfortunately, most SIEM solutions out there often fall short in providing the necessary capabilities to expedite this crucial process. Analysts are left digging through a myriad of related events for each alert, working with multiple tools, and grappling with alert backlogs. This inefficient workflow not only consumes valuable time but also hampers the overall effectiveness of the security operations center (SOC).
Challenges Faced by a SOC Analyst
- Operating Multiple Tools: SOC analysts typically work with a multitude of technologies, including Endpoint Detection and Response (EDR), Network Detection and Response (NDR), deception technologies, and IT operations tools.
- Inability to Prioritize Threats: SOC analysts struggle with alert backlogs, inconsistent alert review and escalation processes, and a lack of sufficient audit trails to understand why certain incidents and/or alerts were closed or overlooked.
- Information Overload: SOC analysts often find themselves overwhelmed with numerous pathways to investigate, making it difficult to pick one and finish them within the SLAs.
An Expert’s Journey to Validating Threats
A skilled SOC analyst possesses the ability to connect the dots and build relationships between artifacts such as IP addresses, usernames, and Tactics, Techniques, and Procedures (TTPs). Based on our interactions with SOC teams and their top performers, here is how they do it manually:
- Assessing Normal Behavior: Analysts examine the normal behavior of applications or services for which an alert has been raised. They compare it with past alerts related to the same target (IP, domain, user, or host) and analyze the timeline of events and alerts.
- TTP Attribution: SOC analysts attribute alerts to specific Tactics, Techniques, and Procedures (TTPs) commonly associated with threat actors.
- Eliminating Repeated Alerts: Suppress repeated or known docile alerts.
- Enrichment and Contextualization: SOC analysts leverage internal metadata and external threat intelligence to enrich alerts with additional context and insights.
While few analysts excel at this pattern recognition process but not everyone.
Closing the Divide with HYPERCLOUD’s Magic
The journey of a master SOC analyst is built upon years of experience, honing their skills in threat validation and investigation. But what if these capabilities could be made accessible to the entire security operations team? That's where DNIF HYPERCLOUD comes in, with its magical powers of closing the divide and empowering every team member to validate threats with precision.
DNIF introduces several innovative features that differentiate it from other SIEM solutions out there:
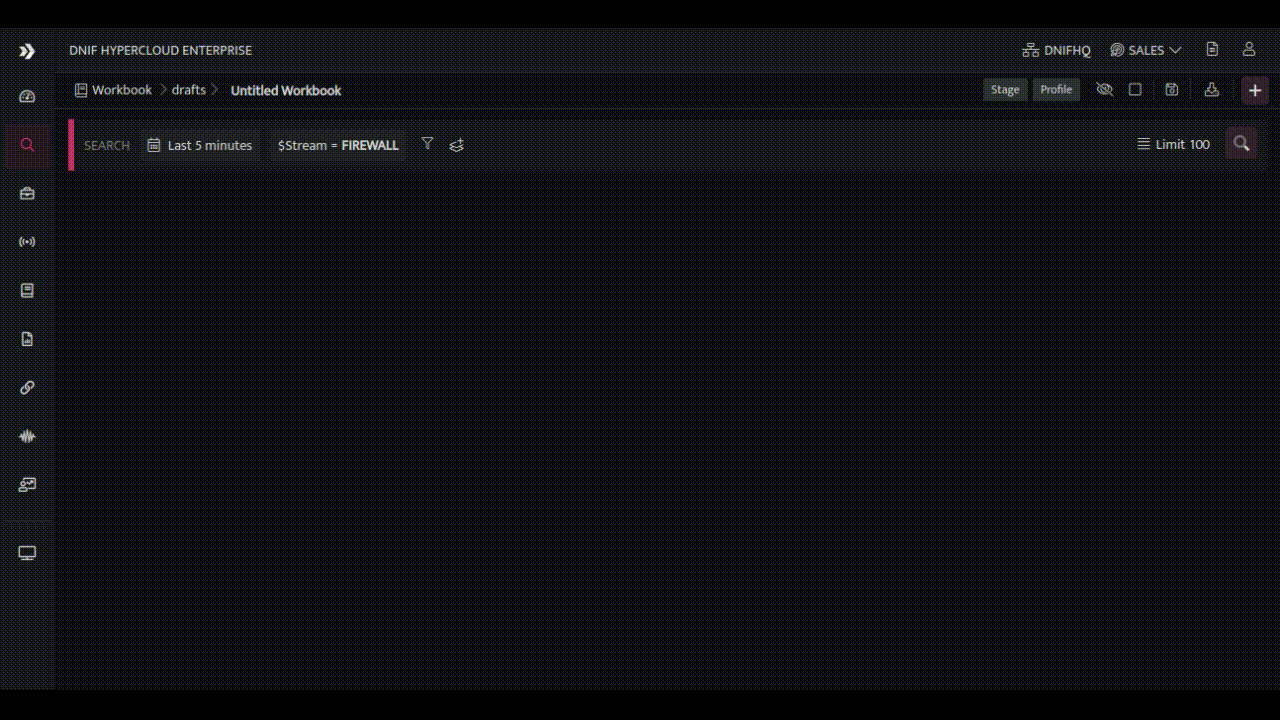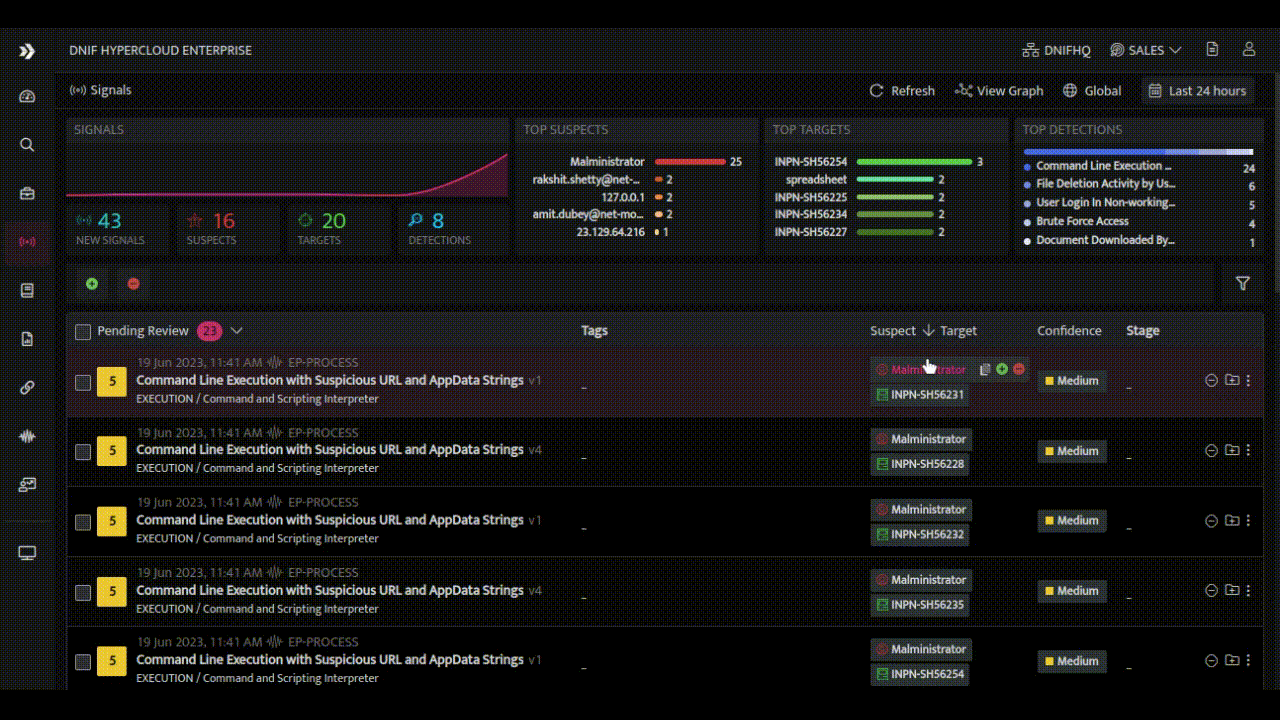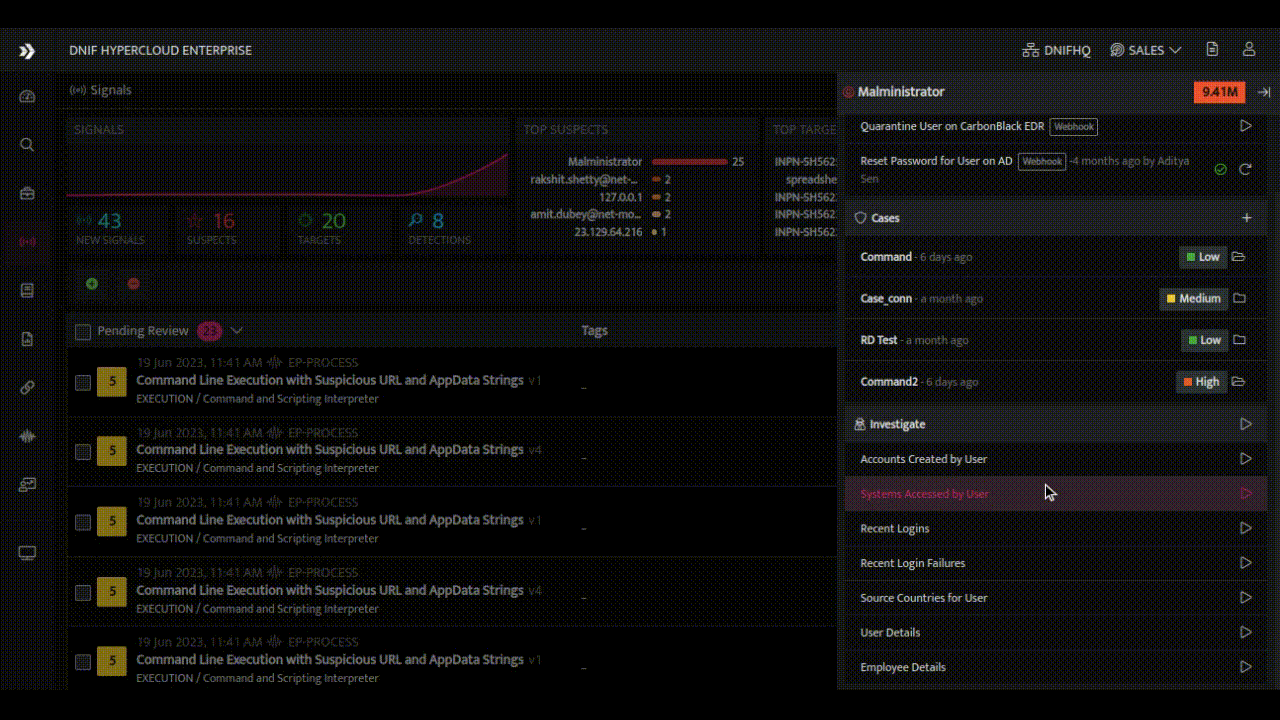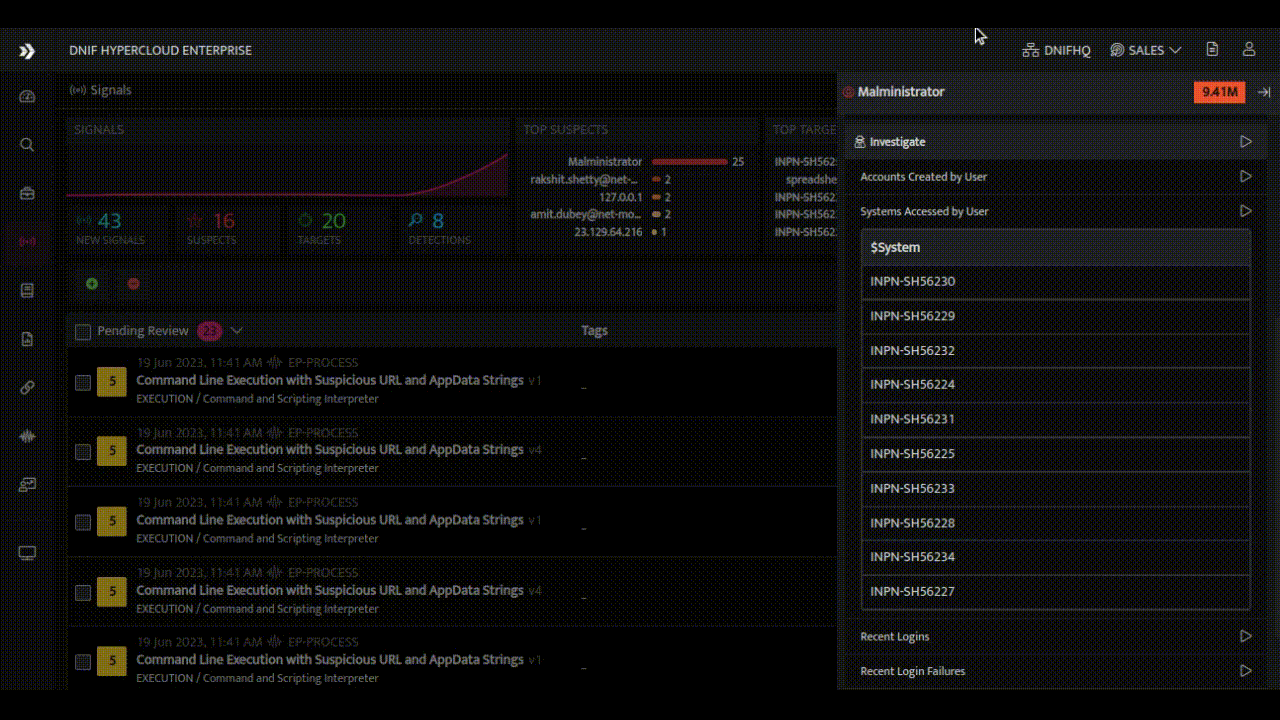
- Alert Consolidation and Relationship Building: The HYPERCLOUD curates multiple alerts and establishes relationships between them, providing a holistic view of threats. This clustering approach allows analysts to identify patterns, prioritize and triage faster.
- Enriched Investigation Panels: The HYPERCLOUD offers an investigation panel that combines raw events related to an alert with various enrichment options and response playbooks. Analysts can access comprehensive information within a single interface, enhancing their efficiency.
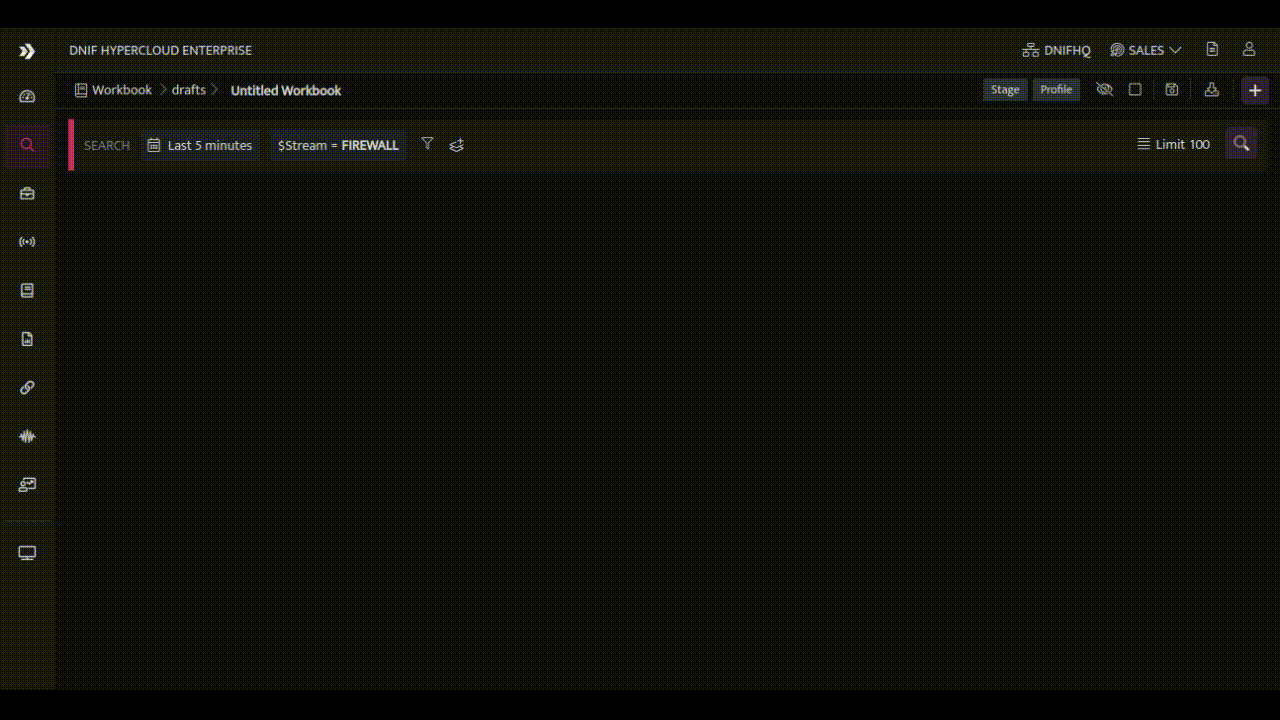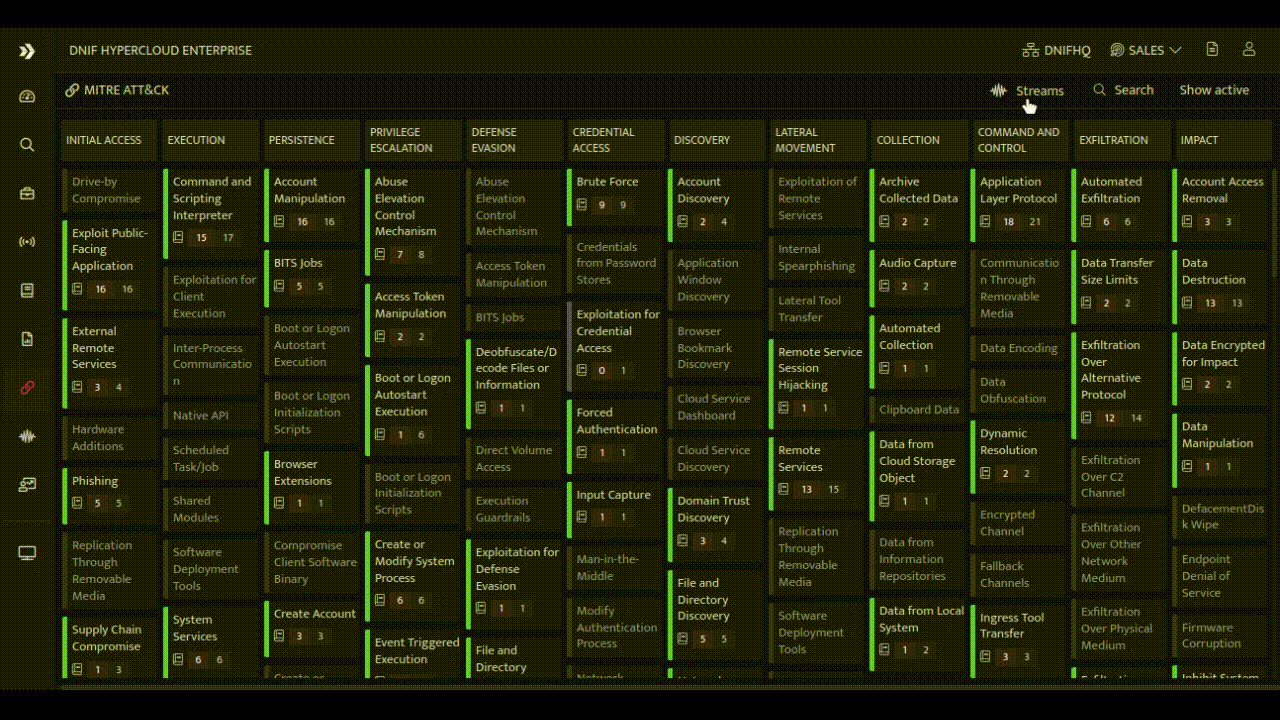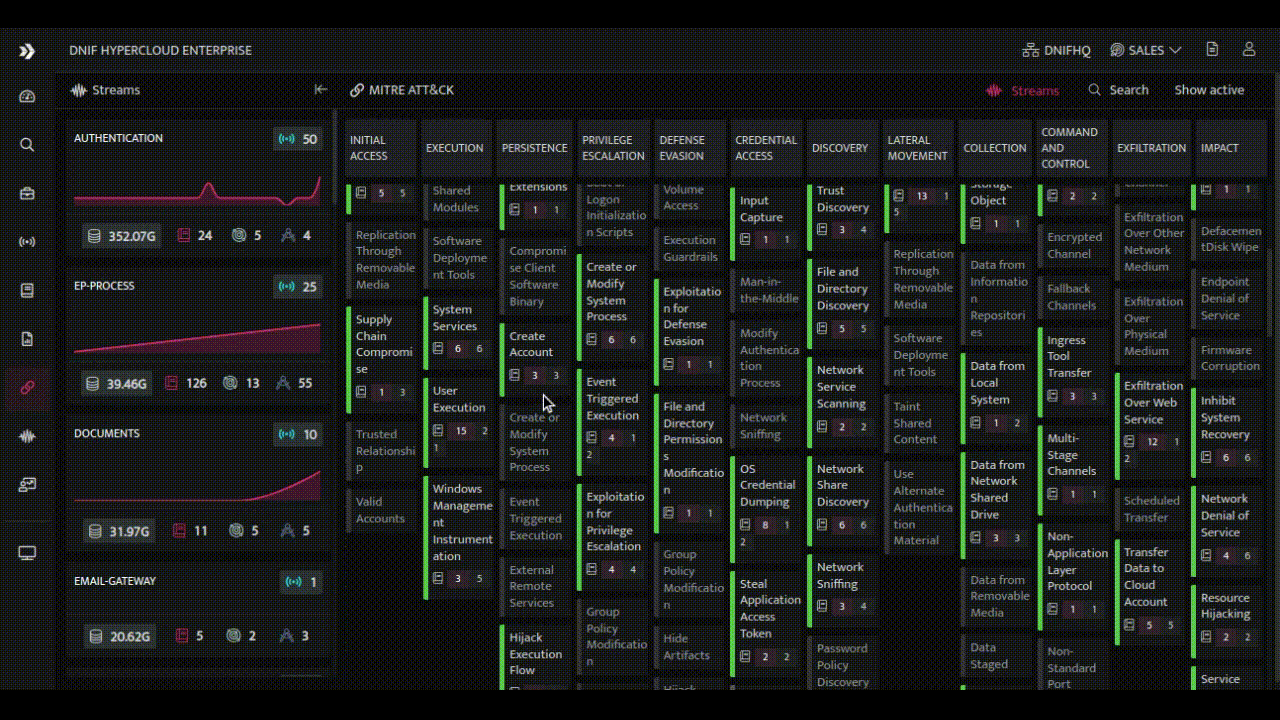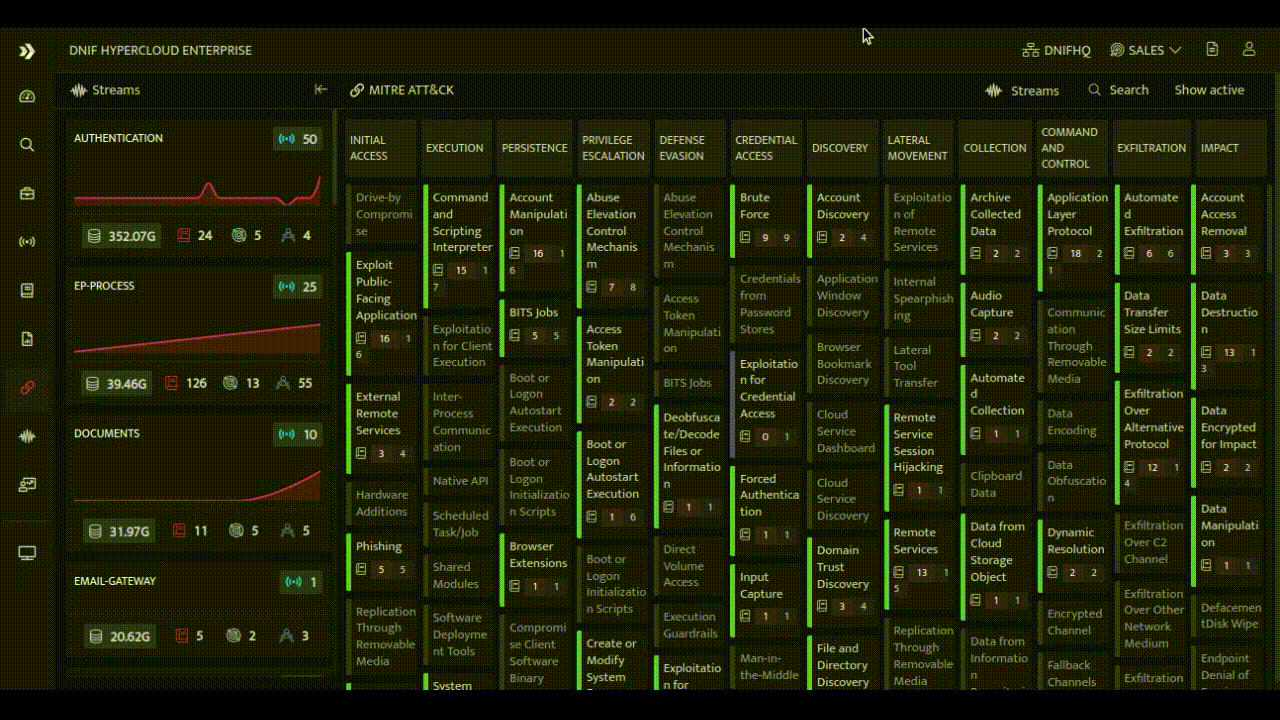
- Visual TTP Mapping: The HYPERCLOUD presents TTP attribution in a visual and intuitive manner through its interactive MITRE ATT&CK page. Analysts can explore the interconnectedness between alerts and TTPs.
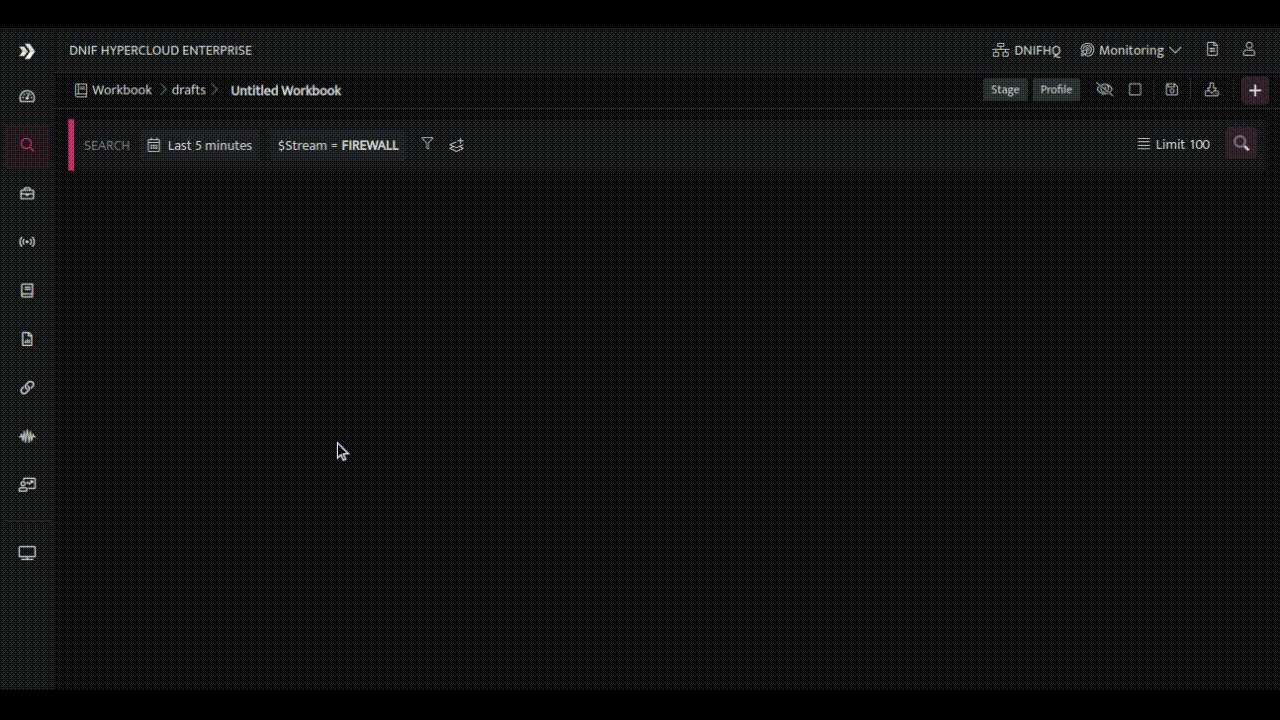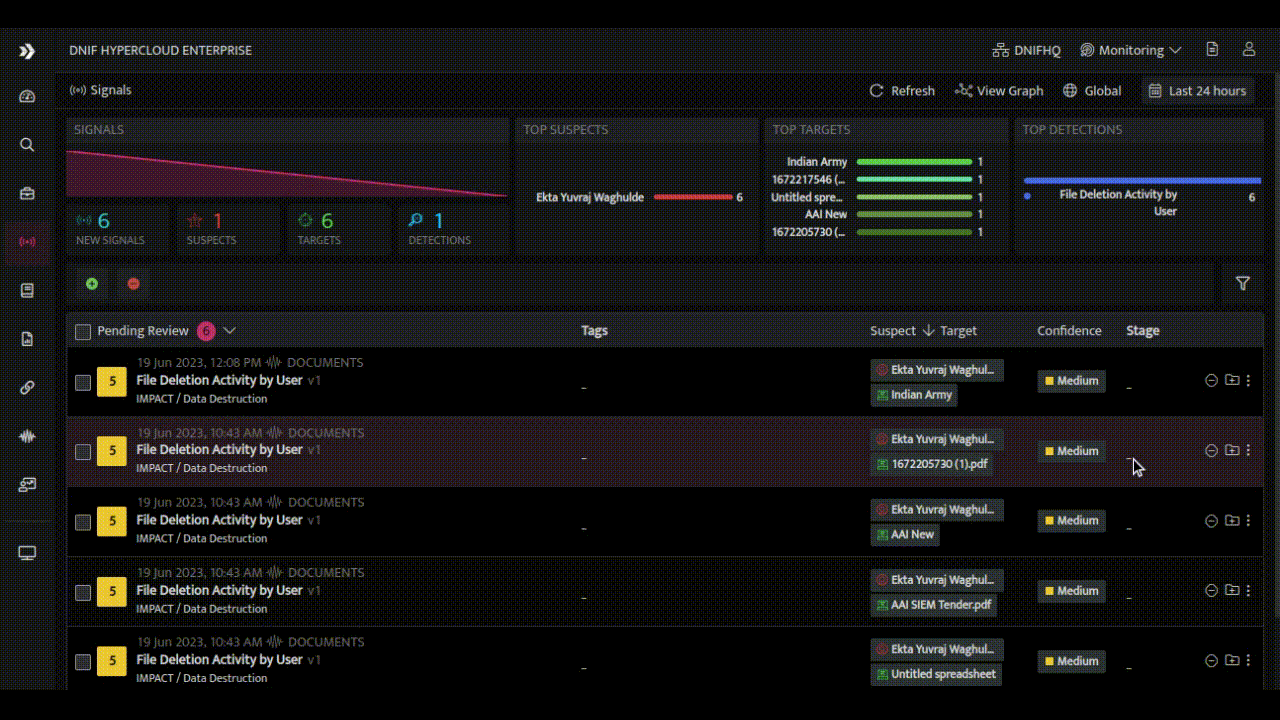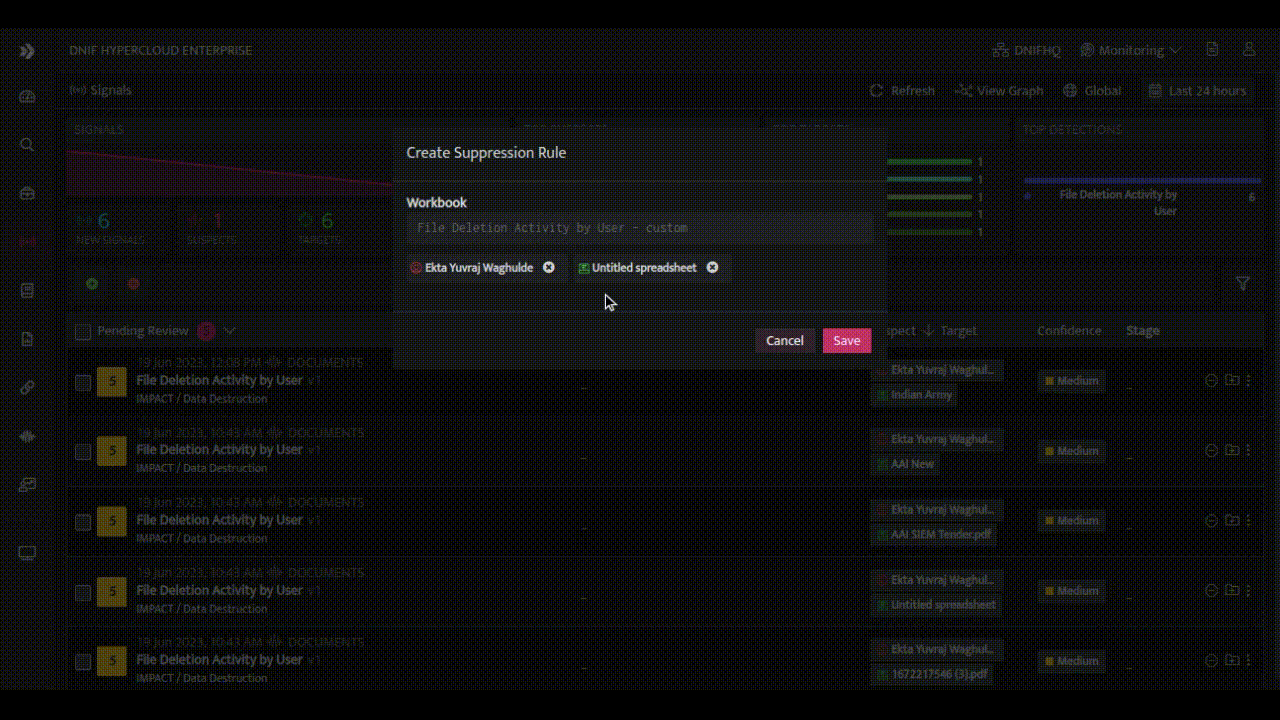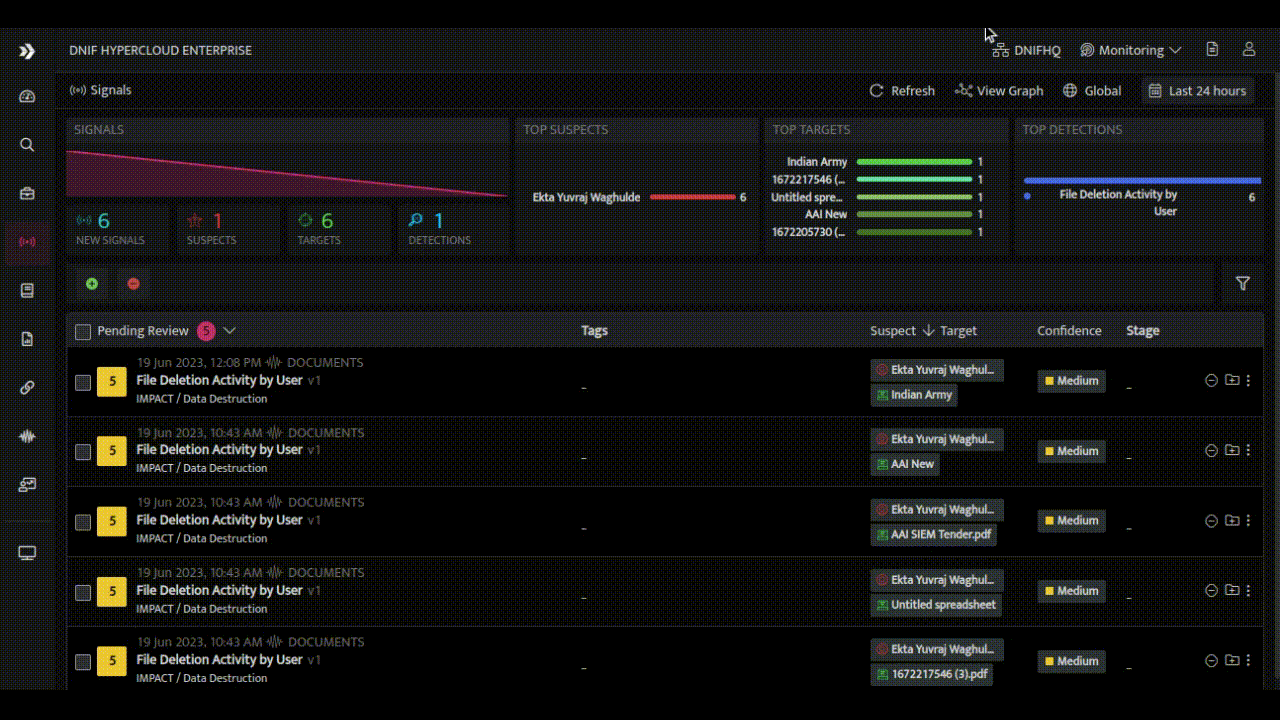
- Eliminating Repeated Alerts and False Positives: The HYPERCLOUD offers various combinations to create suppression rules, such as selecting a target or suspect and specifying attributes like host, user, resource, IP address, or port number. By specifying these parameters, alerts originating from the defined sources will be suppressed. Analyst’s can also mark a signal as false positives for known activities encountered, let's say during pentest or vulnerability scans or administrative activity.
- Timeline Analysis: The HYPERCLOUD presents a timeline of related alerts for a specific target during case investigation, enabling analysts to understand the chronological sequence of events, visually map attack patterns, and identify recurring TTPs across multiple alerts. and gain valuable context during investigations.
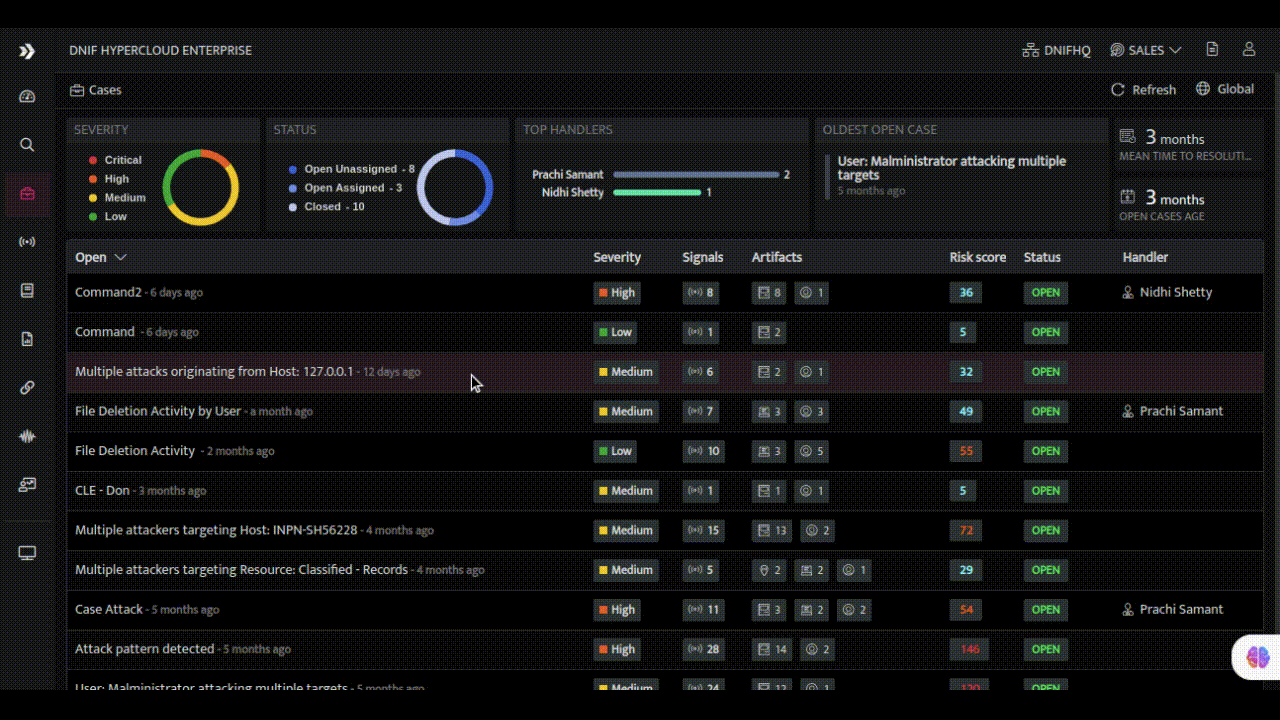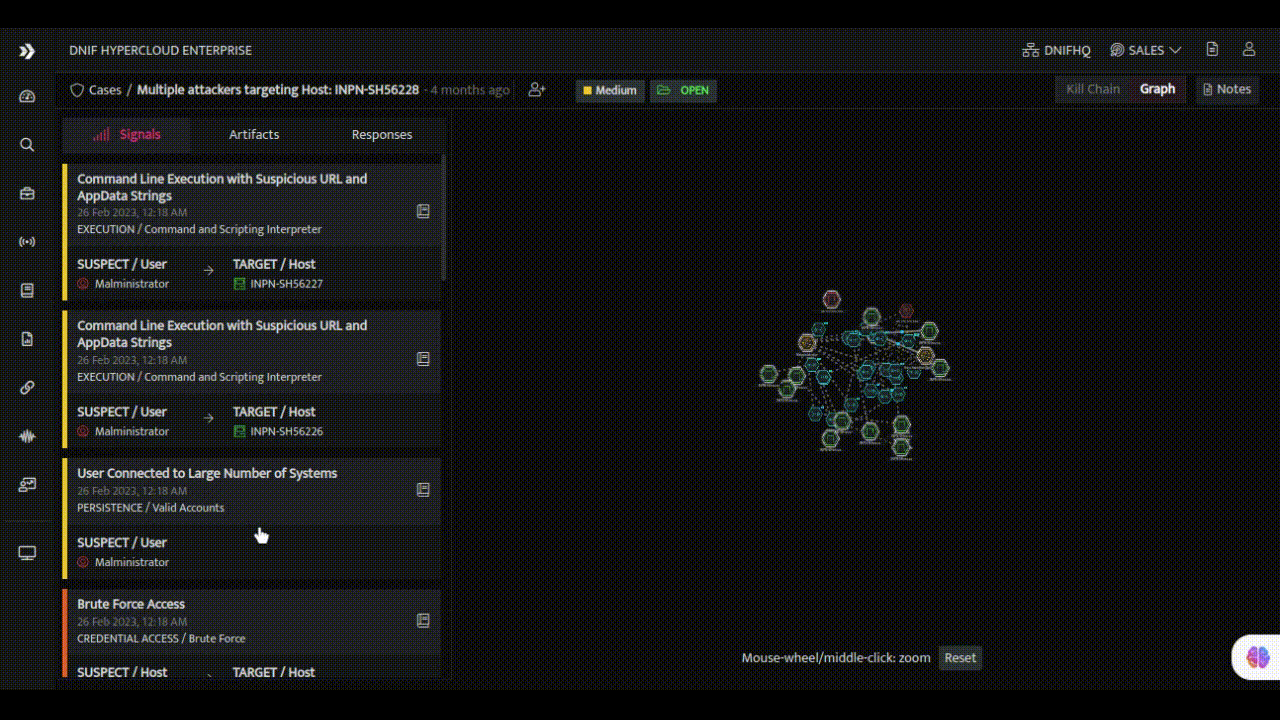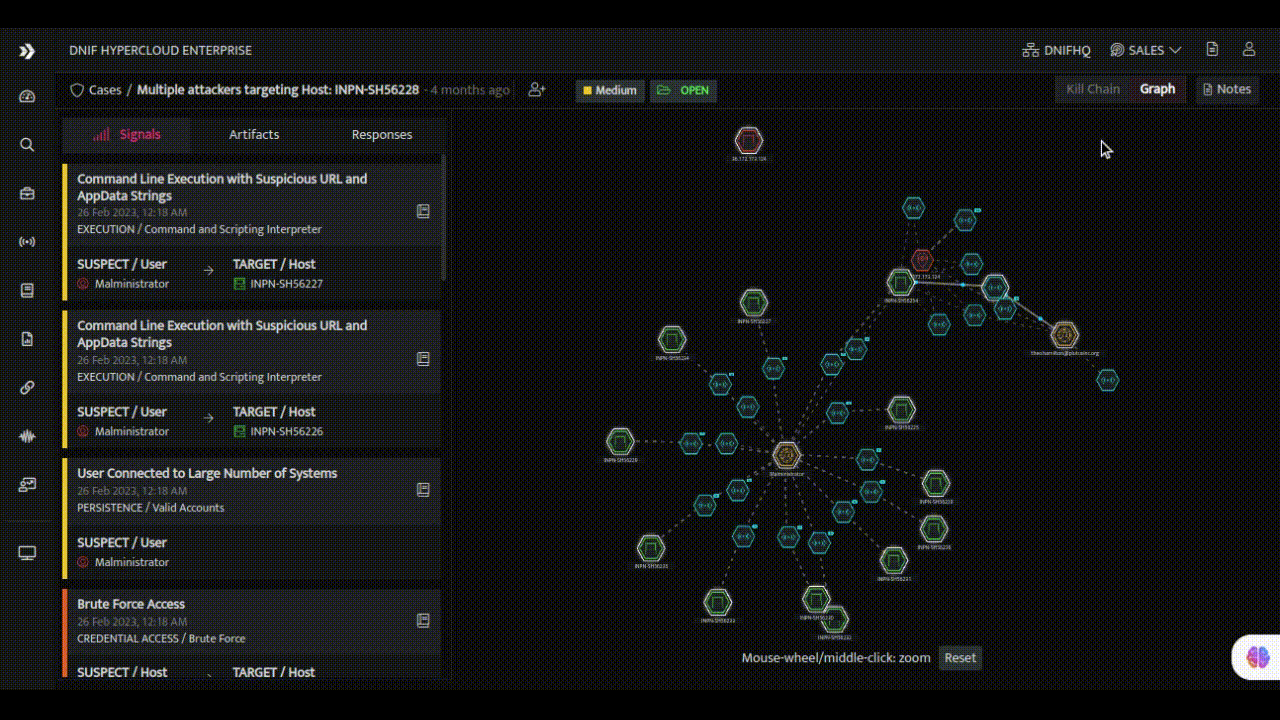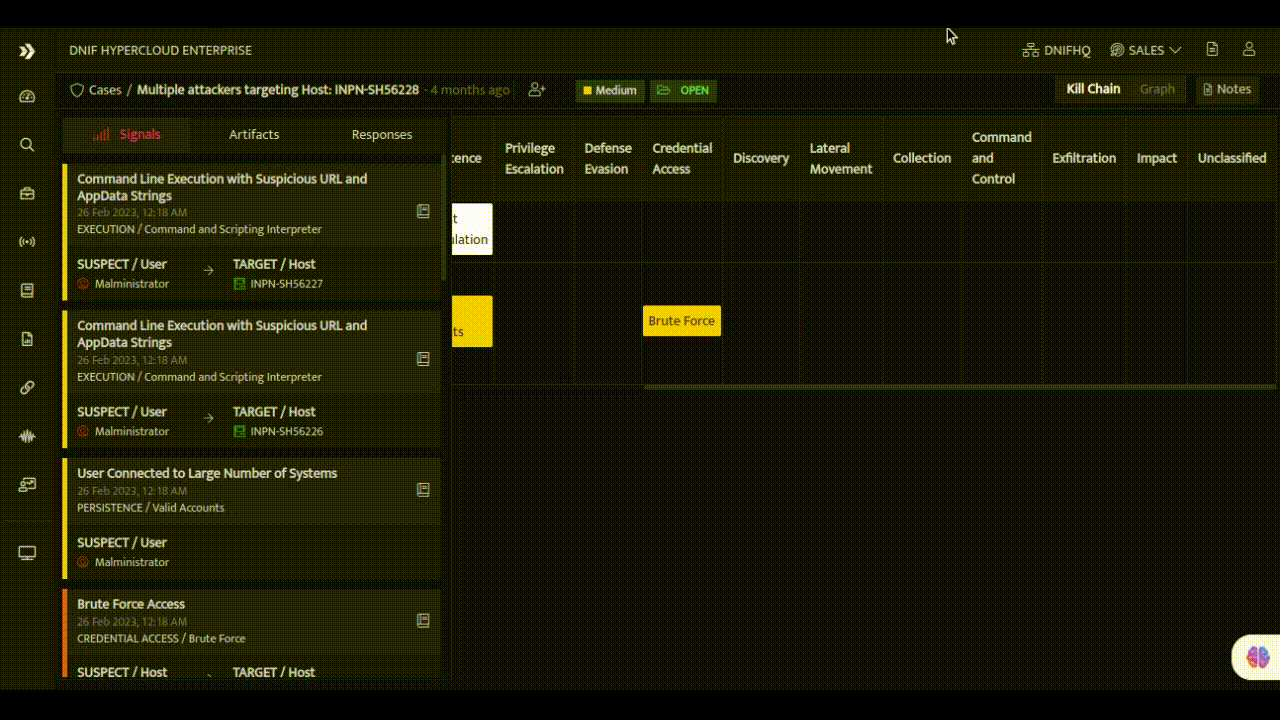
- Enrichment and Contextualization: Enriching alerts with additional context and insights is a hallmark of expert SOC analysts. DNIF HYPERCLOUD empowers every team member with the ability to leverage internal metadata and external threat intelligence sources for enrichment. Through a seamless integration of these resources, alerts are transformed into valuable pieces of information, providing a deeper understanding of the threat landscape and enabling better-informed decisions.
Take Away
The era of the lone master SOC analyst is over. DNIF HYPERCLOUD closes the divide, democratizing the expertise and capabilities that were once confined to a select few. Every team member becomes a part of the master's journey to validating threats, empowered by the magic of HYPERCLOUD. Together, they form an unstoppable force, ready to defend against evolving cyber threats and safeguard the organization's security posture.

