The trend of this ransomware has been observed since November 2021, and in the last quarter of 2022, its name was listed among the top three most prevalent variants. Very quickly it gained its name in the list of professional ransomware families.
BlackCat is more effective among other ransomwares due to its capability to target a wider range of systems. This adversary is written in ‘RUST’ and is capable of targeting both Windows and Linux platforms. Rust is considered as a more secure, high performance and reliable programming language to run concurrent processing. It aided the ransomware to accomplish encryption with fast performance and its capability of efficient memory management. It also makes it difficult to analyze ransomware in the SandBox environment compared to other commonly used languages. It also has an advantage of lower detection ratio from static analysis tools that are usually not adopted to all programming languages.
In the FLASH alert published by FBI in April 2022, it was explained that BlackCat aka ‘AlphaV’ gains initial access to target system with using compromised authentication credentials and it leverages the user access in Active Directory and configure malicious GPO (Group Policy Objects) with Task Scheduler to deploy its ransomware payload.
Once payload gets deployed, the ransomware disables the security within the targeted network to exfiltrate the data and information before its execution. The ransomware uses multiple PowerShell and batch scripts to spread the infection.
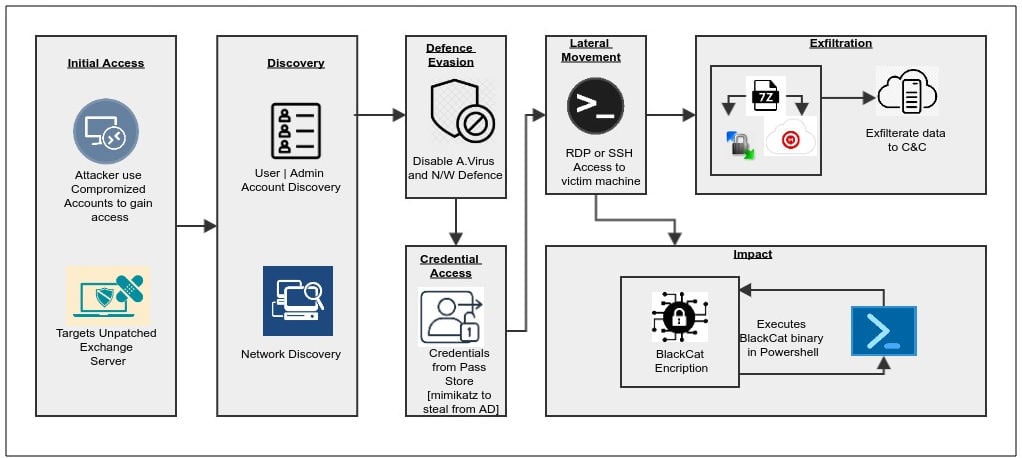
BlackCat Infection chain
In a test campaign done by AT&T labs, they observed that like its previous variants that were observed in 2021. In the case of virtual hosts, it first aims to kill any running virtual machine to ensure that no other parallel infected instances are doing encryption to avoid data corruption.
Unlike regular servers, a virtual machine host can share the same hard-disk with multiple instances.
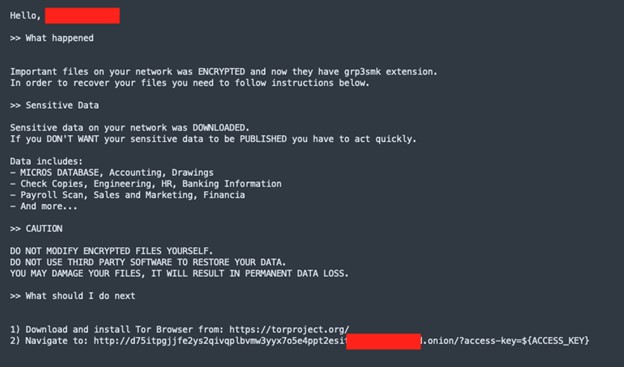
Sample ransom note
(AT&T Labs)
In its preparation procedure BlackCat ransomware also observed doing following steps and templet commands -
-
It deletes Shadow-Copy volumes to remove any data backup copies.
vssadmin.exe Delete Shadows /all /quiet -
It diables any recovery from BDC-Store.
bcdedit.exe /set {default} recoveryenabled No -
It changes the value of network request to its maximum size 65535 in registry hive to enable accessing multiple files during the encryption process.
reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters /v MaxMpxCt /d 65535 /t REG_DWORD /f
-
It also attempts to propagate its payload to multiple systems in the network. For this it runs psexec.exe command from %TEMP% path and leverages its parents execution permission.
psexec.exe -accepteula \\{Target} -u {user} -p {password} -s -d -f -c {payload}.exe {inherited execution flags} -
In the end, it clears windows-event-logs to hide its activity trace.
cmd.exe /c for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"
Detection
-
With realtime Windows Eventlog and Sysmon logs, the execution of .exe file name and SHA256 hash can be matched from below given IoC table.
-
On Windows systems, this ransomware kills below given services that modify files during their execution to avoid data corruption before executing the encryption process.
AcronisAgent, AcrSch2Svc, backup, BackupExecAgentAccelerator, BackupExecAgentBrowser, BackupExecDiveciMediaService, BackupExecJobEngine, BackupExecManagementService, BackupExecRPCService, BackupExecVSSProvider, GxBlr, GxCIMgr, GxClMgrS, GxCVD, GxFWD, GXMMM, GxVss, GxVssHWProv, memtas, mepocs, msexchange, MSExchange, MSExchange$, MVArmor, MVarmor64, mysql, mysql$, PDVFSService, QBCFMonitorService, QBDBMgrN, QBIDPService, SAP, SAP$, SAPD$, SAPHostControl, SAPHostExec, SAPService, sophos, sql, sql$, svc$, veeam, VeeamDeploymentService, VeeamNFSSvc, VeeamTransportSvc, VSNAPVSS, vss, WSBExchang
Associated IOCs
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
f2b3f1ed693021b20f456a058b86b08abfc4876c7a3ae18aea6e95567fd55b2e |
Windows BlackCat Payload |
|
SHA256 |
cefea76dfdbb48cfe1a3db2c8df34e898e29bec9b2c13e79ef40655c637833ae |
Windows BlackCat Payload |
|
SHA256 |
7e363b5f1ba373782261713fa99e8bbc35ddda97e48799c4eb28f17989da8d8e |
Windows BlackCat Payload |
|
SHA256 |
f837f1cd60e9941aa60f7be50a8f2aaaac380f560db8ee001408f35c1b7a97cb |
Windows BlackCat Payload |
|
SHA256 |
731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161 |
Windows BlackCat Payload |
|
SHA256 |
7b2449bb8be1b37a9d580c2592a67a759a3116fe640041d0f36dc93ca3db4487 |
Windows BlackCat Payload |
|
SHA256 |
38834b796ed025563774167716a477e9217d45e47def20facb027325f2a790d1 |
Windows BlackCat Payload |
|
SHA256 |
40f57275721bd74cc59c0c59c9f98c8e0d1742b7ae86a46e83e985cc4039c3a5 |
Windows BlackCat Payload |
|
SHA256 |
b588823eb5c65f36d067d496881d9c704d3ba57100c273656a56a43215f35442 |
Windows BlackCat Payload |
|
SHA256 |
f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89 |
Windows BlackCat Payload |
|
SHA256 |
0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479 |
Windows BlackCat Payload |
|
SHA256 |
c5ad3534e1c939661b71f56144d19ff36e9ea365fdb47e4f8e2d267c39376486 |
Windows BlackCat Payload |
|
SHA256 |
7154fdb1ef9044da59fcfdbdd1ed9abc1a594cacb41a0aeddb5cd9fdaeea5ea8 |
Windows BlackCat Payload |
|
SHA256 |
658e07739ad0137bceb910a351ce3fe4913f6fcc3f63e6ff2eb726e45f29e582 |
Windows BlackCat Payload |
|
SHA256 |
5bdc0fb5cfbd42de726aacc40eddca034b5fa4afcc88ddfb40a3d9ae18672898 |
Windows BlackCat Payload |
|
SHA256 |
c8b3b67ea4d7625f8b37ba59eed5c9406b3ef04b7a19b97e5dd5dab1bd59f283 |
Windows BlackCat Payload |
|
SHA256 |
bd337d4e83ab1c2cacb43e4569f977d188f1bb7c7a077026304bf186d49d4117 |
Windows BlackCat Payload |
|
SHA256 |
28d7e6fe31dc00f82cb032ba29aad6429837ba5efb83c2ce4d31d565896e1169 |
Windows BlackCat Payload |
|
SHA256 |
15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed |
Windows BlackCat Payload |
|
SHA256 |
4e18f9293a6a72d5d42dad179b532407f45663098f959ea552ae43dbb9725cbf |
Windows BlackCat Payload |
|
SHA256 |
13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31 |
Windows BlackCat Payload |
|
SHA256 |
c3e5d4e62ae4eca2bfca22f8f3c8cbec12757f78107e91e85404611548e06e40 |
Windows BlackCat Payload |
|
SHA256 |
1af1ca666e48afc933e2eda0ae1d6e88ebd23d27c54fd1d882161fd8c70b678e |
Windows BlackCat Payload |
|
SHA256 |
3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83 |
Windows BlackCat Payload |
|
SHA256 |
722f1c1527b2c788746fec4dd1af70b0c703644336909735f8f23f6ef265784b |
Windows BlackCat Payload |
|
SHA256 |
d767524e1bbb8d50129485ffa667eb1d379c745c30d4588672636998c20f857f |
Windows BlackCat Payload |
|
SHA256 |
aae77d41eba652683f3ae114fadec279d5759052d2d774f149f3055bf40c4c14 |
Windows BlackCat Payload |
|
SHA256 |
be8c5d07ab6e39db28c40db20a32f47a97b7ec9f26c9003f9101a154a5a98486 |
Windows BlackCat Payload |
|
SHA256 |
9f6876762614e407d0ee6005f165dd4bbd12cb21986abc4a3a5c7dc6271fcdc3 |
Windows BlackCat Payload |
|
SHA256 |
79802d6a6be8433720857d2b53b46f8011ec734a237aae1c3c1fea50ff683c13 |
Windows BlackCat Payload |
|
SHA256 |
2cf54942e8cf0ef6296deaa7975618dadff0c32535295d3f0d5f577552229ffc |
Windows BlackCat Payload |
|
SHA256 |
bacedbb23254934b736a9daf6de52620c9250a49686d519ceaf0a8d25da0a97f |
Windows BlackCat Payload |
|
SHA256 |
3c8ad2dae0b1bb536925b4e8d5a87e77c6134371eada2c7628358d6c6d3083dc |
Windows BlackCat Payload |
|
SHA256 |
67d1f4077e929385cfd869bf279892bf10a2c8f0af4119e4bc15a2add9461fec |
Windows BlackCat Payload |
|
SHA256 |
5a604a8f0e72f3bf7901b7b67f881031a402ab8072269c00233a554df548f54d |
Windows BlackCat Payload |
|
SHA256 |
6660d0e87a142ab1bde4521d9c6f5e148490b05a57c71122e28280b35452e896 |
Windows BlackCat Payload |
|
SHA256 |
f8c08d00ff6e8c6adb1a93cd133b19302d0b651afd73ccb54e3b6ac6c60d99c6 |
Linux BlackCat Payload |
|
SHA256 |
5121f08cf8614a65d7a86c2f462c0694c132e2877a7f54ab7fcefd7ee5235a42 |
Linux BlackCat Payload |
|
SHA256 |
3a08e3bfec2db5dbece359ac9662e65361a8625a0122e68b56cd5ef3aedf8ce1 |
Linux BlackCat Payload |
|
SHA256 |
f7a038f9b91c40e9d67f4168997d7d8c12c2d27cd9e36c413dd021796a24e083 |
Linux BlackCat Payload |
|
SHA256 |
9802a1e8fb425ac3a7c0a7fca5a17cfcb7f3f5f0962deb29e3982f0bece95e26 |
Linux BlackCat Payload |
References
-
AT&T Labs for screenshots/images.
-
Virustotal (IOC Source)

