Table of Content
- Introduction
- Lessons Learned from Successful MITRE ATT&CK & SIEM Integration
- Conclusion
Introduction
MITRE ATT&CK is a widely- used and accepted framework by the cybersecurity professionals in understanding the dynamics of the industry and the various threats prevailing in cyberspace. It is a knowledge base framework that provides a comprehensive solution and customizable approach to identifying and responding to potential attacks. The MITRE Framework serves as a guide, offering detailed information on various attack models, techniques and mitigation strategies for security professionals to build on in improving their cybersecurity program. Using this framework as a guide organizations can look at improving their overall cyber security posture in the industry.
So, explaining in detail, we have today shared some best practices and interesting lessons learned from organizations who have managed to successfully integrate MITRE ATT&CK & SIEM.
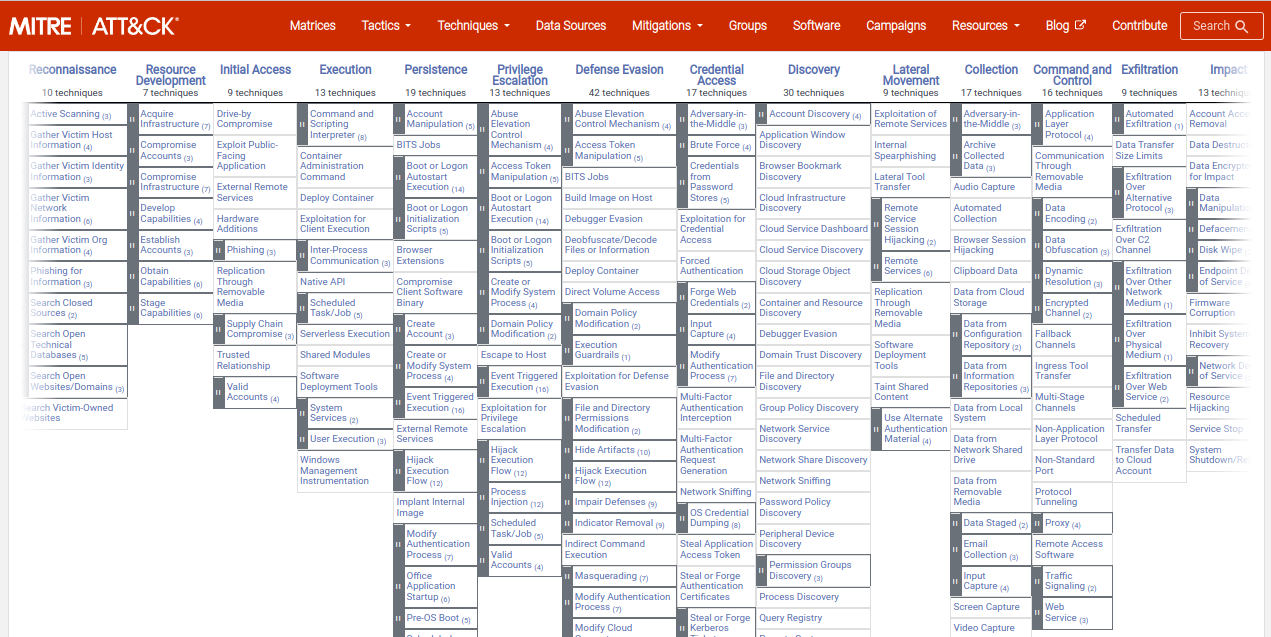
Lessons Learned from Successful MITRE ATT&CK & SIEM Integration
1. Improving SIEM's Effectiveness
One key lesson learned from these organizations is the importance of thoroughly understanding MITRE ATT&CK and how it can be used to improve SIEM effectiveness. In order to get the most out of this framework, security teams need to understand the different matrices, TTPs, and IOCs that are included in MITRE ATT&CK, and how they can be used to analyze and prioritize alerts from their SIEM system. Although this would require significant investment of time and resources, it can pay off in the long run by helping the team to quickly and accurately identify and respond to potential threats.
2. A Roadmap For Continued Security Strengthening
Organizations must realize the need for continued improvement in their security posture. As the threat landscape is constantly evolving, it is essential to develop new detection rules in the SIEM. MITRE ATT&CK framework proves to be a roadmap for this activity. Keeping the MITRE ATT&CK knowledge base up to date, and regularly reviewing and updating the rules and filters in the SIEM system, enables the organizations to safeguard their infrastructure from pertinent threats. This will ensure that the system is able to detect and respond to the latest threats, and the possibility of missing important alerts.
3. Following Best Practices
There are several checks and balances that organizations follow to ensure a successful MITRE ATT&CK-SIEM integration. In doing so, organizations implement necessary best practices and improve their SOC. For example, one of these best practices is to involve all relevant stakeholders in the process, including security analysts, IT personnel, and management during the process of MITRE ATT&CK alignment. This can ensure that everyone understands the process of a structured security framework, benefits and limitations of MITRE ATT&CK, and that there is a shared understanding of how it should be used to improve the organization's cybersecurity posture.
4. Precise and Clear GOALs
An important best practice is to establish clear goals and metrics for the MITRE ATT&CK-SIEM integration. This can ensure that the integration is focused on meeting the specific needs of the organization, and that it is aligned with the overall cybersecurity strategy. By setting specific goals and metrics, organizations can measure the effectiveness of the integration and identify areas for improvement.
5. Need of a PHASED Approach
MITER ATT&ACK is an extensive, detailed framework. It can become a daunting and painful task for an organization to integrate it with its existing security systems. It is advisable that organizations consider using a phased approach to implementing the MITRE ATT&CK-SIEM integration. This can ensure that the integration is successful and that it does not disrupt the existing cybersecurity operations. By starting with a small, focused implementation and gradually expanding it over time, organizations can minimize the risks of disruption and downtime, while the benefits of the integration.
6. Choosing the RIGHT Security Products
Any security device or technology that collects or analyzes security-related data can potentially use the MITRE ATT&CK framework to improve its effectiveness in detecting and responding to cyberattacks. Therefore the ability of the particular device to map its capabilities with the MITRE ATT&CK framework can be crucial in the continuous process of SOC improvement. Organization's should consider this crucial factor while choosing any cyber security solution for their SOC.
Let's take SIEM products for example.
Many SIEM products do not have live mapping of their detection rules with the MITER ATT&CK framework. This makes it challenging to extrapolate what the SIEM can do and then cross-referencing the same with the framework. So, evaluating and considering all aspects and features of a security product is essential when selecting a security tool or product for your SOC.
However, in case of DNIF HYPERCLOUD - you see the security coverage you already have and all that is needed to be done - on the platform itself! DNIF HYPERCLOUD is a dynamic tool that meets all the security requirements of a SOC team. It is a single platform for all your security operational needs, offering the entire security coverage you need and already have for running the SOC efficiently and effectively. This cloud native SIEM makes it easy for the SOC team to strategize and plan their further actions to increase their security coverage. (Click here to know more about DNIF HYPERCLOUD's MITRE ATT&CK alignment.)
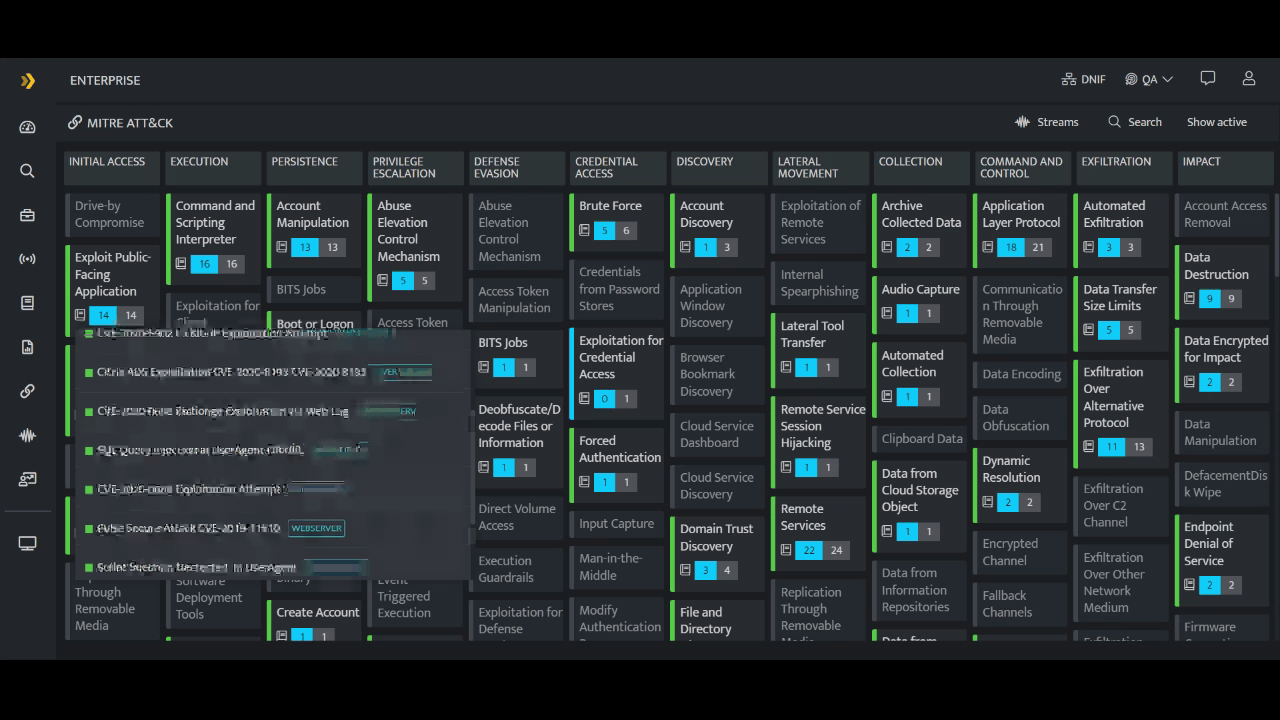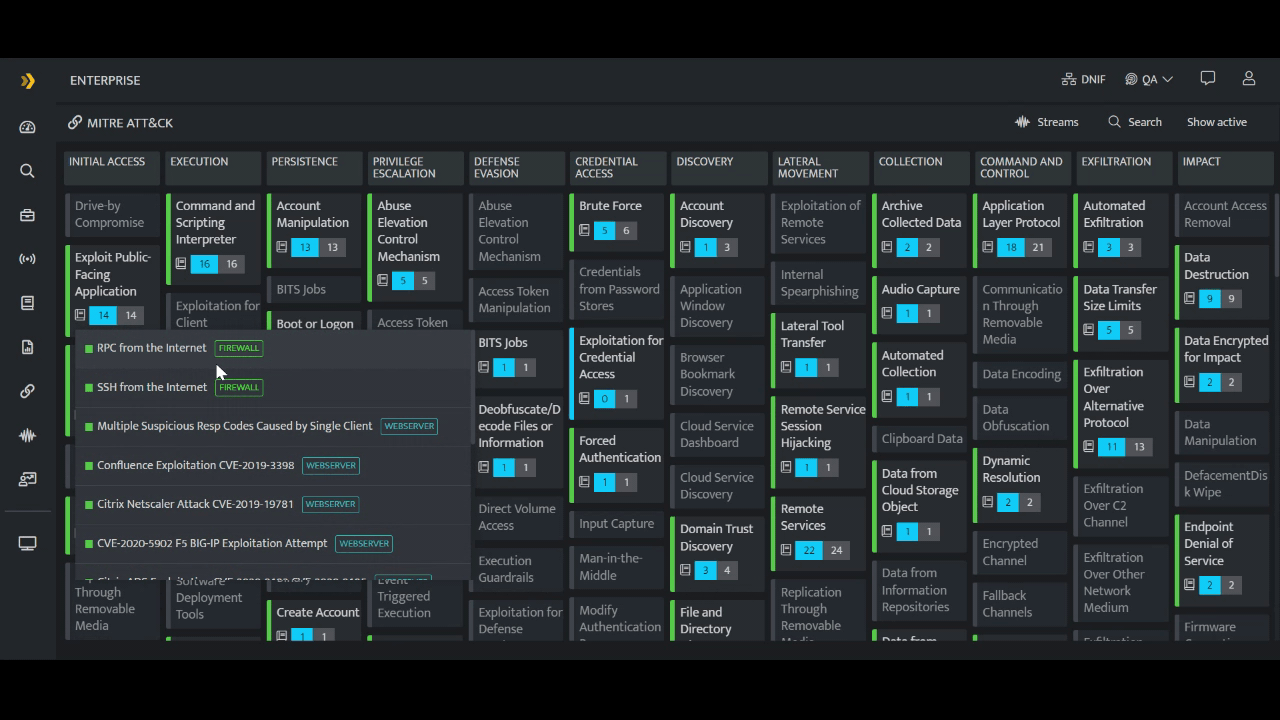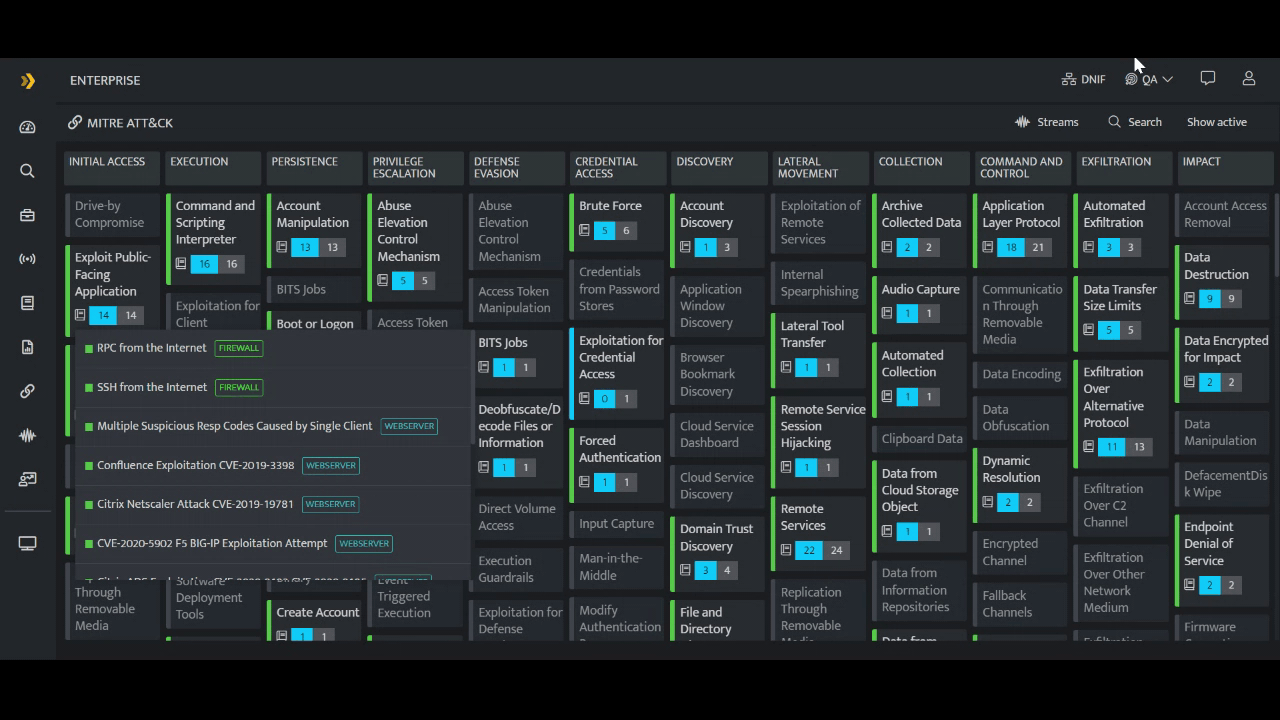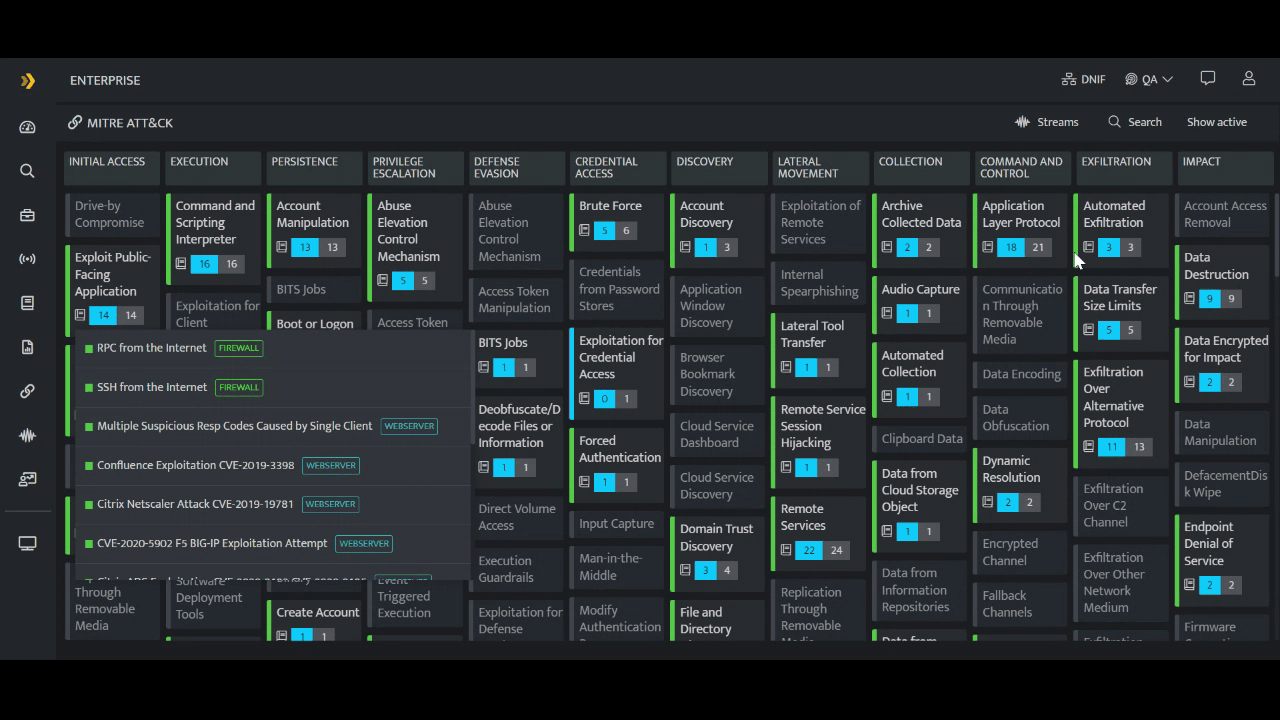
You can also read our blog “Using MITRE ATT&CK to Enhance Threat Hunting & Incident Response”
Conclusion
In conclusion, integrating MITRE ATT&CK with a SIEM system can provide significant benefits for organizations looking to improve their cybersecurity posture. By following best practices and learning from the experiences of others, organizations can avoid the common pitfalls in the process of integration. This also goes a long way in helping the organizations build strong cybersecurity programs.

