Security incidents are becoming more common and complex, putting immense pressure on security teams to quickly identify and respond to threats. With the overwhelming amount of alerts generated by security tools, teams are facing alert fatigue, which occurs when they become desensitized to alerts due to their high volume and false positive rate. However, the complexities of alert analysis do not arise only from the sheer volume. One of the major factors affecting a security analyst's precision in threat detection is the complexity of event logs. To understand the reason behind this complexity, let's understand how the log data is represented in most of the SIEM solutions.
Whenever any SIEM produces parsed log data, all that analysts receive is a string of information under various field names or metadata. For example, a log stream will contain source IP, destination IP, network traffic direction, source hostname, destination hostname, amongst other fields. Amongst these fields lie several important pieces of information, such as firewall action fields.
In the following image, we can see that the firewall event log field [ logid ] gives several codes representing different actions the particular firewall has executed.
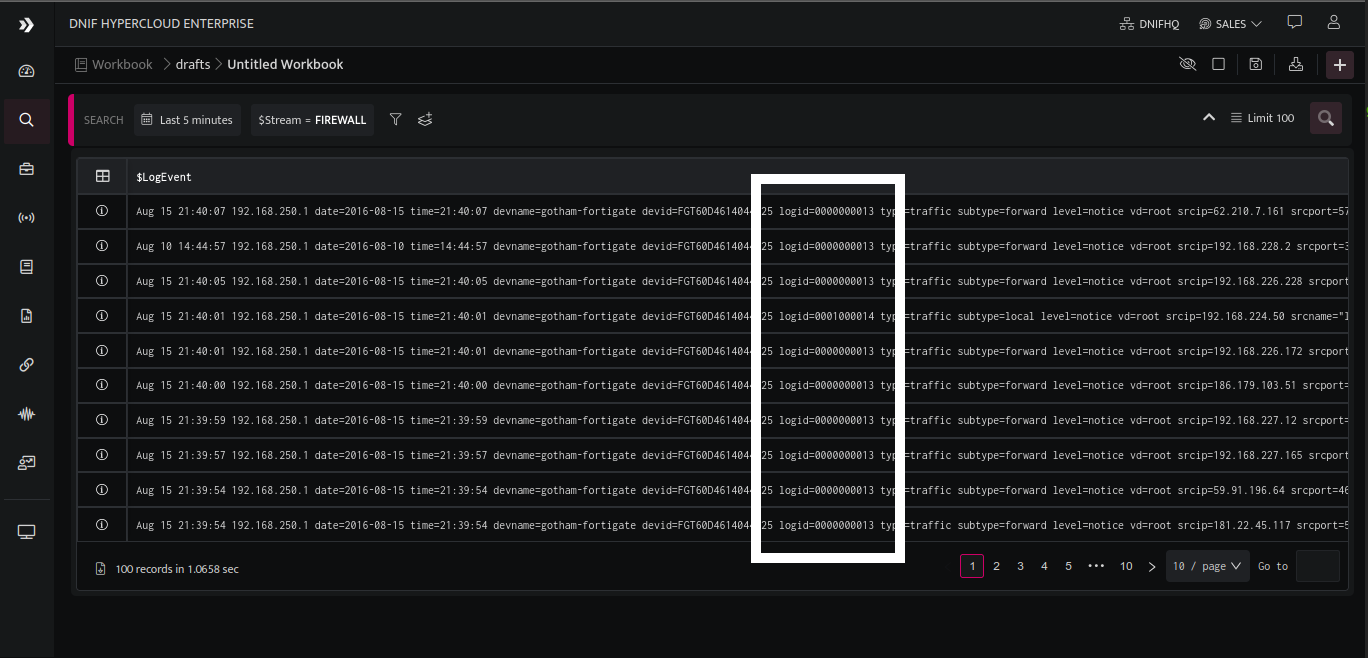
The data at this stage does not give any actionable insight unless the exact significance that each particular code represents is known. How can this be done? By maintaining a cheat sheet for every error code (in this example, firewall's cheat sheet for all the action codes), then pulling out all the incidents with relevant action codes, and then hunting for events based on these error codes. Analysts over time collect and maintain their own personal library of error codes.
While the most critical job is to take an action depending upon the firewall code, security analysts spend most of their resources (attention, focus, and time!) in finding and deciding what all action codes mean. Firewalls have hundreds of action codes. There are 10s of firewalls and 100s of devices are integrated to the SIEM. This results in tremendous volume of events being generated per second. Due to this, security analysts invest most of their time in understanding of meanings of several action codes. This increases the probability of missing out on a critical threat indicators through the vast amount of data churn.
DNIF's innovative Annotations solve this exact problem with precision.
DNIF HYPERCLOUD maps all the action codes from various devices with respective actions so that analysts do not have to manually search for and find the meaning of individual codes. Just by applying filters at the desired action levels, an analyst can find all the events of that particular action.
Here's how it works:
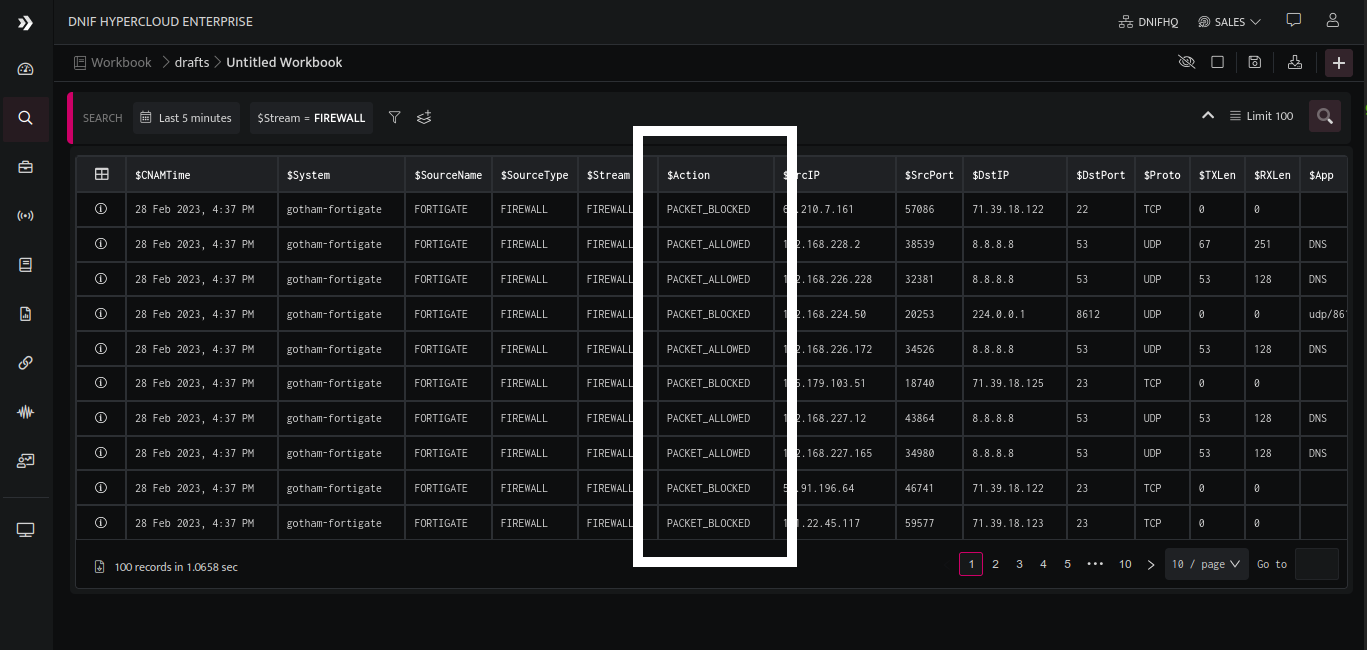
The above image demonstrates how action codes received in the raw log data (highlighted in the previous image) are annotated under the $Action column in the parsed format, with respective meanings of the same.
This Annotation feature has resulted in tremendous value benefits for DNIF customers. The most prominent of which are:
Precision in detection
Manually searching for the meaning of different action ids pertaining to various sources inadvertently results in some misses and gaps in crucial threat intelligence. An analyst is a human being and is prone to get tired after looking at minute pieces of data for hours. After a certain point, there's a great chance that a human eye will fail to capture crucial security threat intelligence. DNIF has used the power of programming innovatively to enable an analyst to hunt for each and every action item with exact precision.
Hours per analyst saved
Getting a dump of all the action codes of all the devices and then searching for the respective action is like searching for a needle in a haystack. It is extremely time-consuming. Imagine the whole team of analysts working on different sets of data to find the actionable insights. Whereas DNIF's Annotations does this job in a matter of seconds - not for one analyst, but for the whole team! Whether it's a packet blocked action or a login failure, a user passed or a remote login, all action codes are mapped and presented in user understandable texts. This saves the organization enormous amounts of man-hours that are put to better use in taking necessary action to prevent the threats.
Optimized efforts
Perhaps the most valued benefit of DNIF HYPERCLOUD Cloud SIEM is the analysts' effort optimization as a result of annotations. The resource hours to be consumed by the team are limited. Therefore, exactly where those efforts are directed becomes paramount if the security posture is to be strengthened at the highest possible level. It is not at all ideal for an organization if the resources are invested in just finding meanings of different codes. Annotations enable resources to focus their efforts where they should be - not on diving and navigating through cheat sheets - but on threat-preventing actions. With the help of Annotations, analysts can quickly find the actionable event ids and go ahead with their course of action.
DNIF HYPERCLOUD's innovative Annotations feature is a game-changer for security analysts who are struggling with the complexities of event logs. This precision, combined with the ability to save hours per analyst and optimize efforts, provides tremendous value benefits for DNIF HYPERCLOUD customers, allowing them to strengthen their security posture and respond quickly to threats.

