
Security Orchestration,
Automation and Response
Connect different detection and response technologies across the enterprise with a common API backplane to automate your investigation, response and mitigation process.
What is SOAR?
SOAR is short for security orchestration, automation and response. This phrase is applied to technologies that make security operations more efficient by retrieving data and performing common or repetitive actions without human intervention. The specifics vary from one security operations center (SOC) to the next, but typical uses include querying threat intelligence feeds and quarantining suspicious machines.
Security orchestration is all about gathering information from a variety of sources and consolidating it in a useful way. For example, suppose you’ve found a suspicious file. To get an idea of the risk it poses, you want to know the source of the file and whether or not it contains any known malware. Getting these answers manually takes time — you’ll need to dig through some logs to find out where the file came from, and you’ll need to upload it to a service like VirusTotal to find out if it’s infected.
Security automation refers to features that enable software to take action without human intervention. Automation isn’t a replacement for human analysts; instead, it reduces the time analysts spend on simple, repetitive tasks. This lets them spend more time focusing on more complex matters where their attention and expertise are genuinely needed.
By pairing automation with orchestration, you can set up rules to handle some of the most common events as soon as they occur. For instance, you can configure the software to check network traffic against a regularly updated list of malicious domains. If a machine in your environment repeatedly attempts to contact one of these domains, the software can automatically quarantine it until an analyst is available to investigate. In the meantime, the rest of the network is protected from the suspicious endpoint.
How SOAR Works
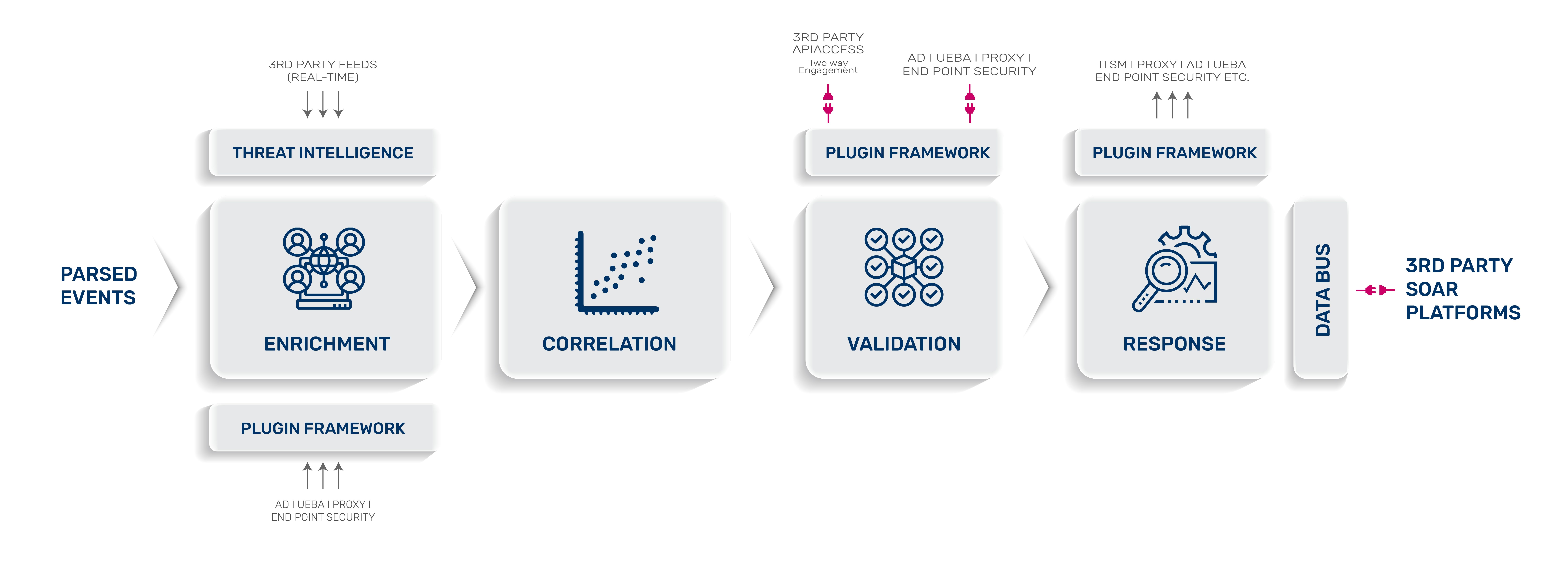
DATA ENRICHMENT
The enrichment phase adds context to events, which makes finding correlations between events easier and more productive. Adding geographical information and whois records are common means of enriching data. However, much more can be done with SOAR:
Advanced examples of event enrichment include:
- Layering a user’s UEBA score on top of Active Directory or proxy events
- Extracting and adding IP context from AD, and adding it to proxy events
- Aggregating third-party threat intelligence and enriching events with context
- Adding user attributes extracted from AD to database users
Adding context makes correlation more productive, enhancing the capabilities of your SIEM platform.
THREAT VALIDATION
Previously, correlation rules were limited to simple models and groupings. There were no opportunities to automatically validate correlation results or incorporate third-party threat intelligence. Today, SOAR can also validate correlations, ensuring that the right decisions are made in the response phase.
By calling on external sources to validate decisions and add context to correlated outcomes, SOAR makes more effective validation systems possible. Examples of ways threats can be validated include:
- Validate domains / IPs / file hash etc using remote threat intelligence providers.
- Validate and contextualize event details with additional fields from either ITSM or Active Directory.
In the validation phase, SOAR reduces investigation time by removing the need for manual checks that differentiate threats from false positives.
RESPONSE
Response is the last phase in the event pipeline. Any event reaching this point has become a confirmed alert that requires action. Cross-verification of the threat has already been performed, so action must be taken to counter the threat.
Traditional systems stop short of this stage, simply raising an incident or ticket on a handler’s screen. It is then the handler’s responsibility to validate and respond to the threat manually. This time-consuming approach lets attackers remain in the system longer than necessary, by modern standards.
Examples of triggerable responses include:
- Raising a ticket in the ITSM application
- Notify users using email or chat apps like Google Hangouts / Slack etc
- Trigger a vulnerability scanner on an unrecognized device
- Choke a process, block disk and network access using an endpoint product
Why you need SOAR?
Automate manual tasks to reduce alert fatigue to focus on threats that really matter and prevent threats to slip through the cracks.
Consistency in human judgement has always been a challenge. Solve this inconsistency by using playbooks to set definite investigation paths.
Trigger a vulnerability scanner, choke a process, block disk and network access on an endpoint product, etc.
Wondering how you could implement an automation framework in your SIEM?
Book a personalized demo to see it in action.
SOAR With DNIF
Customers that Love and Trust us





Ready to make your security operations even better?
See what makes us different. Book your personalized demo today and see DNIF in action.

