Table of Content
- Introduction
- What is Threat Hunting & Incident Response?
- How can MITRE ATT&CK be used for Threat Hunting & Incident Response?
- Conclusion
Introduction
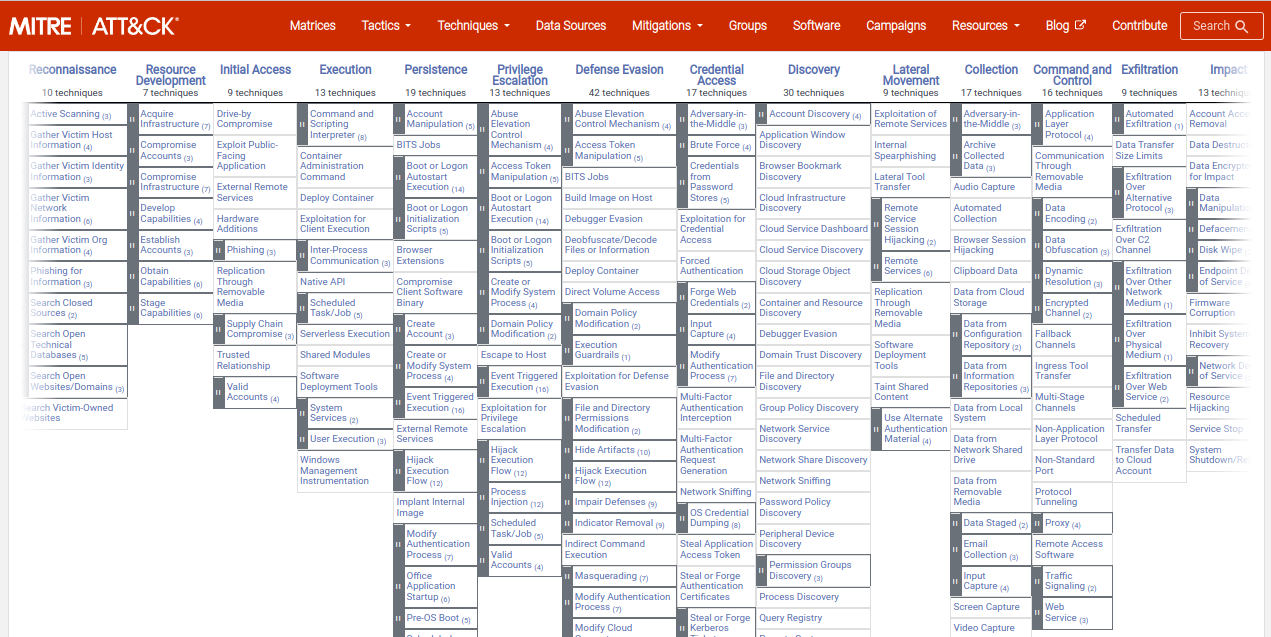
The MITRE ATT&CK framework is a widely-used threat modeling and analysis framework that provides a comprehensive approach to identifying and understanding the tactics, techniques, and procedures (TTPs) used by attackers. Developed by the MITRE Corporation, it is designed to help organizations understand and defend against cyber threats by providing a common language for describing and understanding the tactics and techniques used by adversaries. The MITRE ATT&CK framework covers a wide range of attack scenarios and is organized into different "matrices" that focus on specific types of attacks, such as those targeting cloud environments or mobile devices. Additionally, it provides a set of tools, such as the ATT&CK Navigator, that organizations can use to help identify and prioritize threats based on their specific needs.
Additionally, MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics, techniques, and procedures (TTPs) based on real-world observations. It provides a comprehensive framework for understanding the various stages of an attack and the TTPs used by attackers at each stage. By using MITRE ATT&CK, organizations can enhance their threat hunting and incident response capabilities, improving their ability to detect and respond to security threats.
What is Threat Hunting & Incident Response?
Threat hunting is the proactive search for indicators of compromise (IOCs) within an organization's network and systems. It is a proactive approach to security that involves looking for signs of an attack before it becomes a full-blown incident. By using MITRE ATT&CK as a guide, threat hunters can focus their efforts on the TTPs used by attackers, improving their chances of detecting and responding to threats.
Incident response is the process of responding to a security incident, such as a data breach or ransomware attack. It involves a range of activities, from identifying and containing the threat to recovering from the incident and mitigating any potential damage. By using MITRE ATT&CK as a framework, incident respondents can better understand the TTPs used by attackers, allowing them to respond more effectively to incidents.
How can MITRE ATT&CK be used for Threat Hunting & Incident Response?
MITRE ATT&CK framework is a very resourceful, knowledge base, providing critical details on various types of attacks and attack techniques. Elaborating on this we have shared some ways that organizations can use MITRE ATT&CK to enhance their threat hunting and incident response capabilities:
1. Identify Critical Assets & the Threats Facing your Organisation:
MITRE ATT&CK can help you identify the assets that are most critical to your business, as well as the threats that your organization faces. This will help you focus and prioritize your resources in defending these critical assets against the prevailing threats. Overall, with MITRE ATT&CK your organization can improve their threat hunting and incident response capabilities and prioritize their efforts on the areas that matter most.
2. Map your Existing Controls & Defenses to MITRE ATT&CK
By mapping your existing controls and defenses to the relevant TTPs in MITRE ATT&CK, you can better understand the effectiveness of your current security posture. This will help you identify gaps in your defenses and further take necessary actions to close them.
3. Use MITRE ATT&CK as a Guide for Threat Hunting
When conducting threat hunting, you can use MITRE ATT&CK as a guide to help you focus your efforts on the specific TTPs used by attackers. Using MITRE ATT&CK can enhance the level of accuracy in threat detection and response. It will help you detect potential threats more effectively and respond to them before they cause damage.
4. Use MITRE ATT&CK to inform your incident response plans
When developing your incident response plans, you can use MITRE ATT&CK to help you understand the TTPs used by attackers and plan your response accordingly. This will help you respond more effectively to incidents, minimizing the potential damage and downtime.
(Are you in the process of choosing a SIEM solution for your organization?
BUYER'S GUIDE FOR CLOUD SIEM will help you choose the right Cloud SIEM)
Conclusion
MITRE ATT&CK can be extremely useful to the SOC team when it comes to gauging the security of the environment and the effectiveness of measures established for appropriate threat detection. By using MITRE ATT&CK can help enhance the threat hunting and incident response capabilities which can further facilitate organizations in improving their ability to quickly detect and respond to security threats. Such integrated solutions can also protect critical assets and reduce the likelihood of a successful attack.
DNIF HYPERCLOUD is a native cloud SIEM solution with MITRE ATT&CK alignment that helps you understand your detection coverage, the TTPs that you can detect, and the ones you can't and ones which have detection models but no events for. Click here to book a 45 minute demo of the solution and see how it strengthens your security posture.