Table of Content
- Introduction
- What is MITRE ATT&CK & How it Works?
- How does MITRE ATT&CK Relate to SIEM?
- How can MITRE ATT&CK Improve Threat Detection in SIEM?
- Conclusion
Introduction
MITRE ATT&CK is a widely-used cyber security framework for understanding and detecting cyber threats. Developed by a not-for-profit organization, MITRE, this framework offers a comprehensive and customized approach to identifying and responding to potential cyber attacks. Explaining briefly about the MITRE ATT&CK Framework, we have also shared details on how MITRE ATT&CK relates to SIEM (Security Information and Event Management) systems and how it can be leveraged to improve the efficiency and threat detection accuracy of an SIEM tool. But before that let us learn about MITRE ATT&CK and how it works
What is MITRE ATT&CK & How it Works?
MITRE ATT&CK is a knowledge base of adversarial tactics, techniques, and procedures (TTPs) that can be used to understand the behavior of an attacker in a network. This framework is organized into different "matrices" that focus on specific platforms (e.g. cloud, mobile, endpoint) and adversary groups (e.g. nation-state, criminal, hacktivist). Each matrix includes detailed descriptions of the various TTPs that can be used by attackers on that platform or belonging to that group, along with Indicators of Compromise (IOCs) and other relevant information.
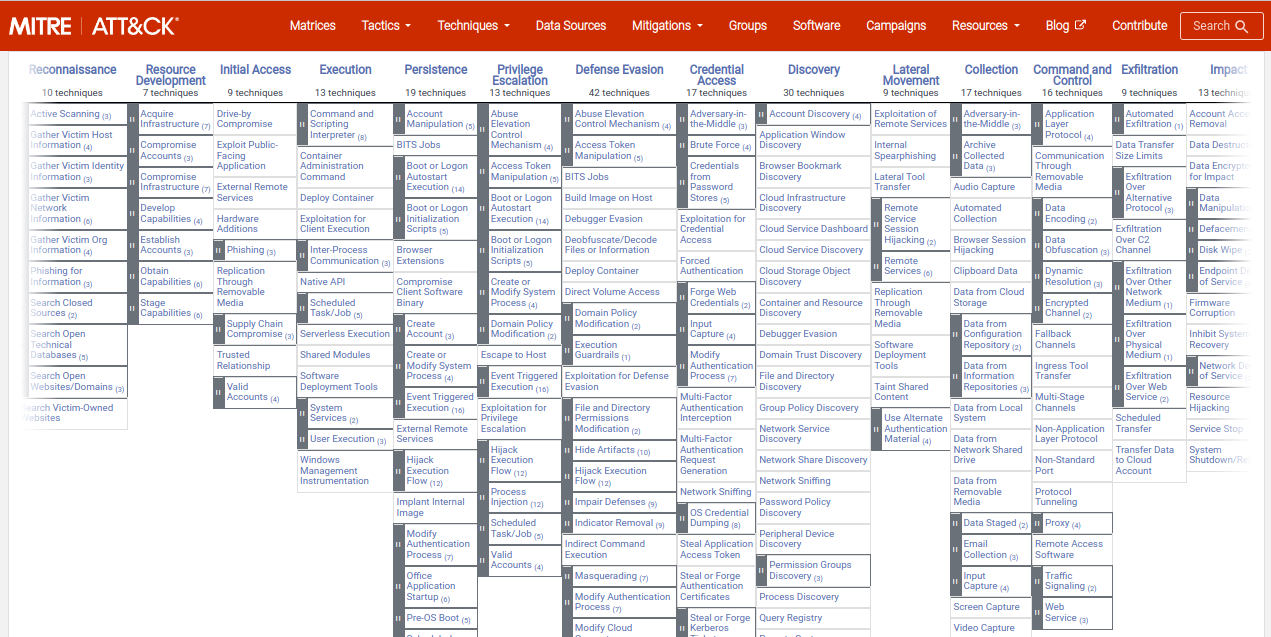
One of the key features of MITRE ATT&CK is that it is openly available and continuously updated. This means that security professionals can access the latest information on known threats and use it to improve their defense strategies.
In addition to this, MITRE ATT&CK is designed to be modular and customizable, allowing organizations to create their own matrices based on their specific needs and threat profiles. Now that we know what MITRE ATT&CK is & how it works, let us move on to understand how it relates to SIEM.
How does MITRE ATT&CK Relate to SIEM?
MITRE ATT&CK can be used as a reference and guideline for configuring and prioritizing alerts in a SIEM system. By mapping the TTPs and IOCs from the MITRE ATT&CK to the alerts generated by a SIEM system, security analysts can gain a better understanding of the potential threats facing their organization. This can further help establish and automate processes for responding to the potential threats detected.
For example, if a SIEM system generates an alert for a specific TTP (e.g. spearphishing) that is known to be used by a particular adversary group (e.g. nation-state), the security analyst can use the information from MITRE ATT&CK to prioritize that alert and automate process for appropriate action. This can help the analysts quickly identify and respond to high-risk threats, and prevent wasting time on false positives or low-priority alerts. Incorporating MITRE ATT&CK into your SIEM strategy can go a long way in improving the efficiency and effectiveness of SIEM solutions. Integrating MITRE ATTACK can improve the ability of your SIEM systems to effectively detect and flag any suspicious activities.
How can MITRE ATT&CK Improve the Effectiveness of SIEM?
In addition to providing a reference for analyzing alerts, MITRE ATT&CK can also be used for improving the overall effectiveness of a SIEM system. By incorporating the knowledge and insights from MITRE ATT&CK, security teams can create more effective rules and filters for their SIEM system. Organizations can configure it to focus on the most relevant and important threats. With this, it can significantly reduce the alert fatigue and the rate of false positives generated by systems. This can help improve the overall efficiency of the SIEM system and strengthen the overall security posture of your organization.
Conclusion
MITRE ATT&CK is a valuable resource for security professionals who wish to stay updated on the latest threats and tactics used by attackers. MITRE ATT&CK updates allow security analysts to stay informed of new threats and help them gauge their current defense systems against the new threats. It can further help the team build a robust security strategy for defending their environment against these new threats. By using MITRE ATT&CK in conjunction with a SIEM system, organizations can improve their ability to detect and quickly respond to potential cyber attacks. It is a way of proactively detecting and protecting the networks and assets of your organization against the evolving threats.
DNIF HYPERCLOUD is a MITRE ATT&CK mapped, Cloud-native SIEM solution that harnesses the power of the mighty knowledge-base, real-world adversary tactics, techniques, and procedures (TTPs). The MITRE ATT&CK alignment helps improve the effectiveness of our cloud-native SIEM (Security Information and Event Management) and enhance the overall ability to detect and respond to security threats. Schedule a demo to witness live - how DNIF HYPERCLOUD not only provides a 360 degree overview of your security posture but also strengthens it multi-fold.

